Introduction
Welcome to Securing 365, a space where I, Cody McLees, will share with you upcoming updates from Microsoft 365, best practices, and things to look out for in your own implementations.
In today’s segment, we will cover the topic of FIDO or USB Security keys.
What are FIDO security keys?
FIDO (Fast Identity Online) keys are typically USB devices that can be physically plugged into a user’s workstation. FIDO keys more commonly now have NFC and Bluetooth as well for scenarios where USB devices are not allowed or not physically available on a workstation or mobile device. FIDO keys are un-phishable meaning they cannot be stolen by a man in the middle attack and cannot be given away virtually to a threat actor like some of the most common attacks on the internet today.
How Do FIDO Security Keys Work?
These security keys are used by end users in both Multi Factor Authentication scenarios and passwordless authentication scenarios. FIDO keys are connected to a user’s identity by a self-service registration in their application where they are also requested to set up a PIN or biometric unlock of the device. Once the device is registered it can be used as a secure and phish-resistant MFA method for users and can even be used to replace the passwords of end users.
Benefits of Using FIDO Security Keys in Microsoft 365
Straight up, Passwords are a problem. Most organizations are behind the times with passwords and are still requiring users to reset their password on a regular basis. NIST has been recommending for 4 years now to make sure you set your password requirements correctly, then change your reset interval to never expire. Studies have proven that expiring passwords leads to poor practices and usage of less secure passwords.
Reasons why passwords should be replaced with security keys ASAP:
- Passwords are knowledge based – FIDO keys are physically based and much more difficult to steal
- Passwords can be difficult to use and remember – FIDO keys don’t change and don’t have to change
- Passwords can be easy to steal, socially engineer, and re-use – FIDO keys cannot be virtually stolen and cannot be intercepted by man in the middle attacks
Implementing FIDO Security Keys in Microsoft 365
Enable FIDO2 keys for Authentication:
To enable security keys for authentication, you will need to go to the Entra Admin center as an Authentication Administrator or greater. You will need to go to the authentication methods page and select policies. Once there, select Passkey (FIDO2).
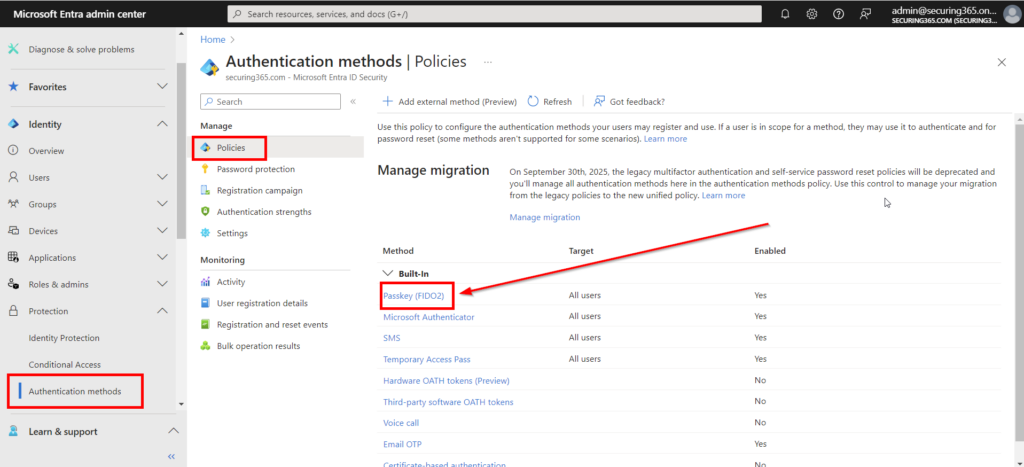
Once there, you can select the users you would want to enable Passkeys for. I typically recommend enabling this for all users as it will not prompt or impact the users, other than allowing them to register keys as an MFA method on future registration setups.
There is a section of optional passkey settings. We won’t dive into these in this blog post, but we will in future ones. If you’d like to read more about the optional settings you can do so here.
Configure FIDO Security Key Authentication Policies:
One your authentication policies are set, you will also want to consider enabling a setting called “System-preferred multifactor authentication.” This setting will make sure that your users are presented with the most secure MFA method they have registered. So, if a user is using SMS for MFA then registers a security key, they will be prompted by the more secure method (security key) for MFA going forward. If this isn’t enabled, that same user would have to adjust their default MFA methods on their own within the My Security Info page.
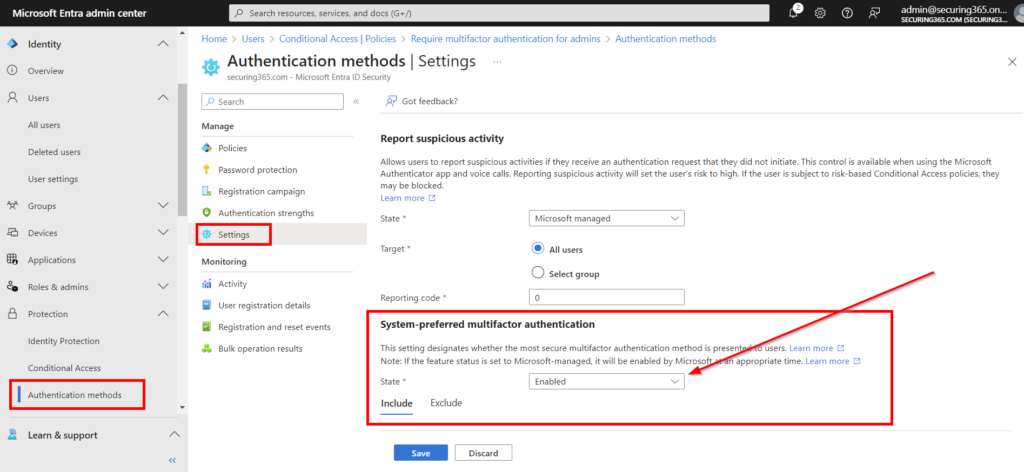
Register FIDO Security Keys:
To register a passkey is super simple. Users will navigate to aka.ms/mysecurityinfo and register a security key.
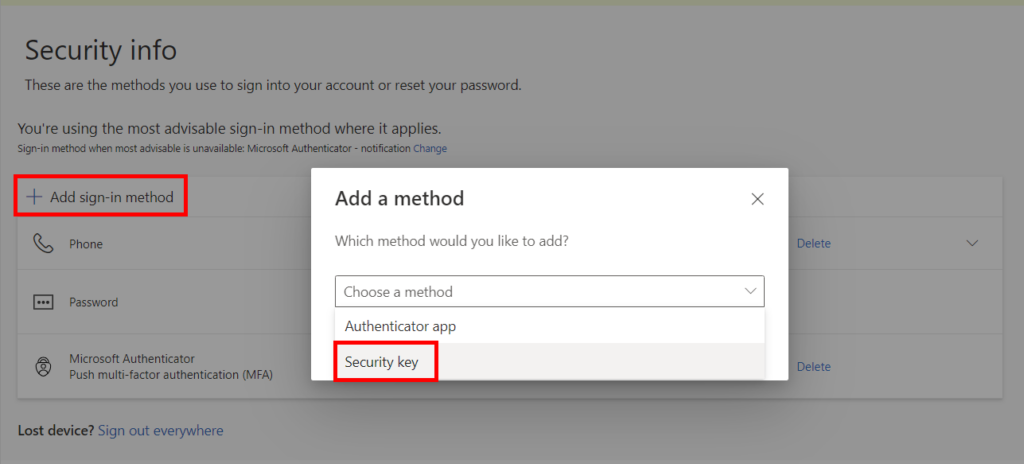
Once selected they will select whether the device is USB or NFC. Some keys can be both, make sure you educate your users based on the hardware selected and the hardware available on their workstation to read the key.
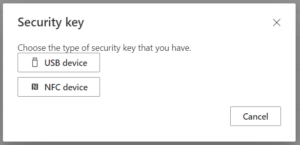
If it’s the first time your users are plugging in a security key, they may be prompted to setup a PIN or fingerprint for the device so it can be unlocked. You’ll want to document this process for your users, so they know what is expected.
A key step, if your users are using Google Chrome, is the next screenshot. Chrome will want to save the passkey itself or have your users use a virtual passkey. Select “save another way” to have it get you to the subsequent screenshots to use an external security key.
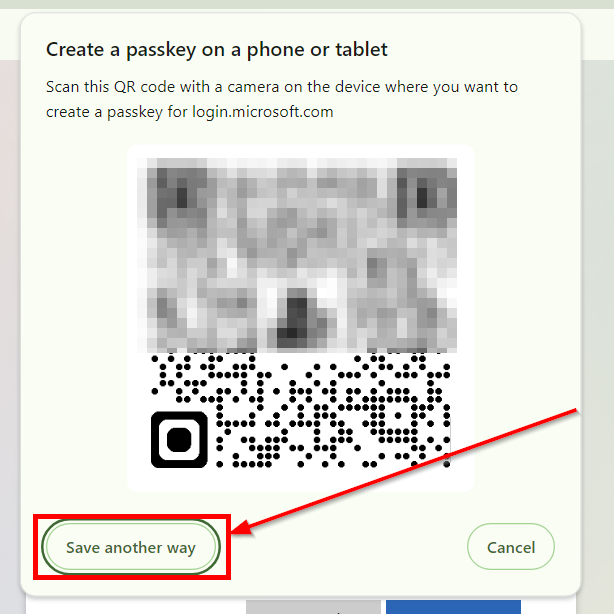
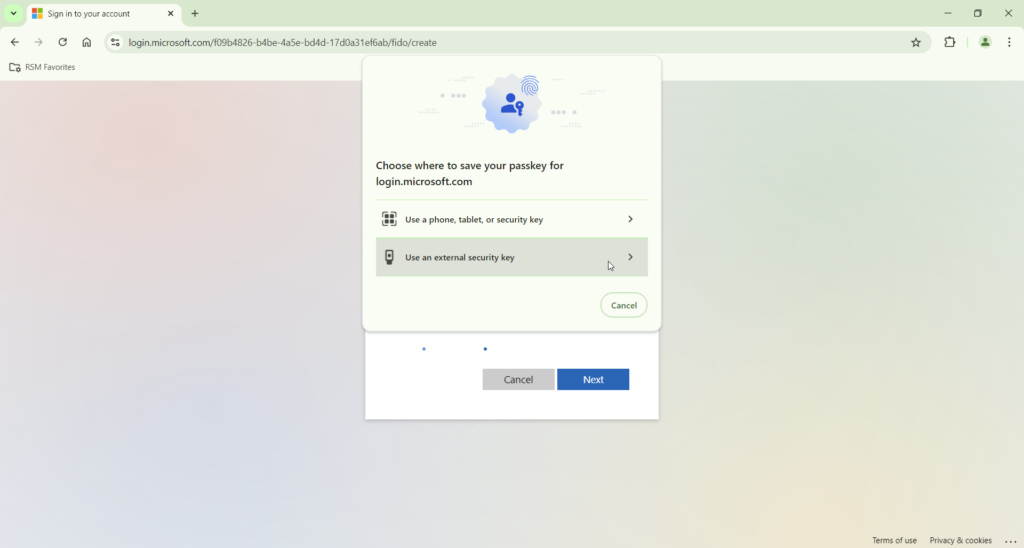
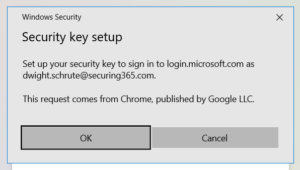
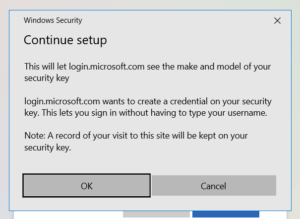
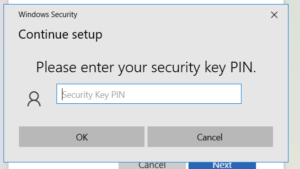
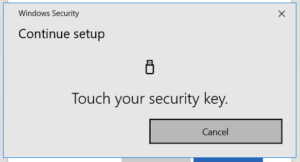
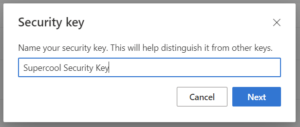
Educate Users:
As with any technological changes, communication will be key. I suggest getting executive buy in for this level of organization change as it can be difficult for users to adopt this or see the additional security. This can also be used as a method of MFA for users who are unable or unwilling to use personal phones for MFA prompts.
I often use the analogy of your car keys, no one can steal your car keys from a malicious drive by web attack. Let’s keep our online accounts the same way.
Best Practices for Using FIDO Security Keys
Deploy in Stages
When deploying to your organization, as mentioned above, executive buy in is key for change, but also super user buy in will be key as well. In the early stages of your deployment, identify your super users in each department or group for deployment and have them be early adopters or pilot users. These users can be the first line of defense on rollout day and can assist their immediate colleagues rather than coming to IT or security for assistance. These users can also talk about the benefits of this coming change before it hits the other users.
Have a Backup Plan:
Security keys are great, but they can also be lost. Have backup plans for when users forget their keys at home, break USB ports, lose their keys, or just forget how to use them. Give your users options for when things are lost, broken, or forgotten. Some examples are below:
- Provision 2 security keys per user
- Allow the usage of an authenticator app as a backup option
- Allow the usage of temporary access passes
Educate Continuously:
Don’t just drop these keys in your user’s laps and run, keep educating them on the benefits of additional security and that these keys can be used for personal accounts too. Also continue to educate your users on the latest cyber threats, email attacks, etc via your normal channels or via your cyber security training platform of choice.
Conclusion
In conclusion, FIDO keys act as a significant step forward in security for your organization. I hope you can use the tips and tricks in this blog post to adopt the usage of these keys to not only secure your users but to drive the path forward toward a passwordless environment.
References
- https://learn.microsoft.com/en-us/entra/identity/authentication/concept-authentication-passwordless#passkeys-fido2
- https://fidoalliance.org/how-fido-works/


