Introduction
Welcome to Securing 365, a space where I, Cody McLees, will share with you upcoming updates from Microsoft 365, best practices, and things to look out for in your own implementations.
In today’s segment, we will cover the newest Microsoft mandates for Multifactor Authentication (MFA) in Microsoft 365.
Fish in a Barrel
Microsoft 365 has been under constant attack since its inception. Some folks refer to users of it as “fish in a barrel” because threat actors know right where to go for email, collaboration, and sensitive information of their targets. Because of this, Microsoft has been pushing more and more security requirements upon their tenants. The latest round is being enforced on 10/15/2024 and will target only specific portals.
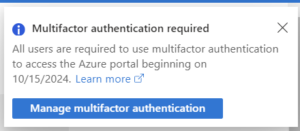
This MFA enforcement only targets specific portals and other portals will be added at later dates. See the full table for the schedule below.
| Application Name | App ID | Enforcement phase |
|---|---|---|
| Azure portal | c44b4083-3bb0-49c1-b47d-974e53cbdf3c | Second half of 2024 |
| Microsoft Entra admin center | c44b4083-3bb0-49c1-b47d-974e53cbdf3c | Second half of 2024 |
| Microsoft Intune admin center | c44b4083-3bb0-49c1-b47d-974e53cbdf3c | Second half of 2024 |
| Azure command-line interface (Azure CLI) | 04b07795-8ddb-461a-bbee-02f9e1bf7b46 | Early 2025 |
| Azure PowerShell | 1950a258-227b-4e31-a9cf-717495945fc2 | Early 2025 |
| Azure mobile app | 0c1307d4-29d6-4389-a11c-5cbe7f65d7fa | Early 2025 |
| Infrastructure as Code (IaC) tools | Use Azure CLI or Azure PowerShell IDs | Early 2025 |
Delaying the inevitable
So what if you can’t, wont, or are afraid of doing MFA? It isn’t recommended, but you do have the option of delaying the enforcement of MFA until March 15th, 2025. At this point, it is likely that Microsoft will force your hand.
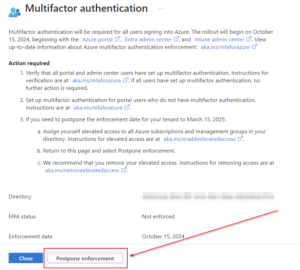
Unknowns
What isn’t well documented or communicated out of all of this is “How is Microsoft Going to Enforce this?” In past enforcements of MFA from Microsoft we have witnessed Conditional Access Policies being dropped into our tenants, however this isn’t the case this time. Microsoft seems to be planning to enforce the MFA requirement via the enterprise applications themselves, making it somewhat difficult to plan for regarding our emergency access accounts. As of the timing of the writing of this article, it appears Microsoft plans to have this be all encompassing without any exclusions of the breakglass or emergency access accounts. We will talk about emergency access accounts and their considerations within Conditional Access later in this article.
Let’s fix this ourselves…
If you don’t already, it would be worthwhile considering doing all of this via a Conditional Access policy and taking it to the next level and protect all of your M365 resources for ANY users with a privileged role. How can we do this? Let’s open Conditional Access and Create a policy.
At the top of the new policy is users. We will select users > Include > Select Users and Groups > Directory Roles. From there we will type “administrator” into the search bar and select all roles that contain the word “administrator.” At the time of this post, this is 73 roles.
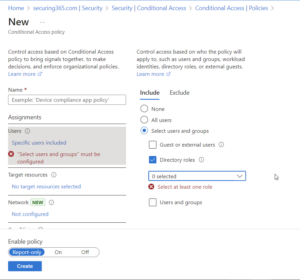
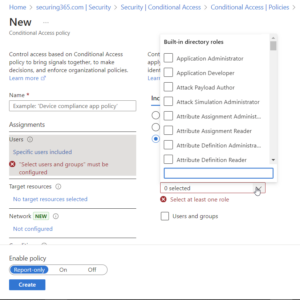
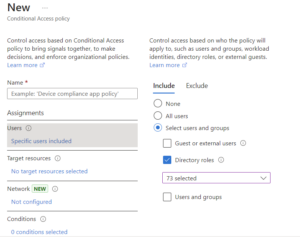
After that, make sure to select “All Cloud Apps” and Select “Require Multifactor Authentication.” If you have emergency access accounts in Microsoft 365, be sure you are excluding/targeting those appropriately. THIS POLICY WILL AFFECT EVERY ADMINISTRATOR IN YOUR ENVIRONMENT. USE WITH CAUTION.
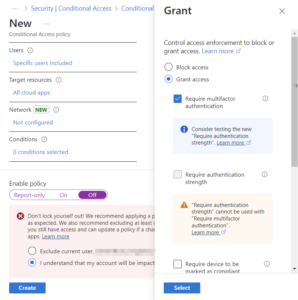
Don’t feel like creating the policy manually? Import this JSON file since I have already done the heavy lifting for you.
Considerations
When creating a policy like the above, you will want to consider your emergency access accounts as I mentioned above. These accounts are typically excluded from your conditional access policies for emergency access in the event the platform has an outage.
Let’s go a step further
FIDO Keys
Rather than relying on application based MFA (which is still better than no MFA) let’s take a look at the authentication strengths feature within our Conditional Access policies. This authentication strengths feature allows us to require “phish-resistant” MFA and require the users targeted with the policy to use FIDO security keys.
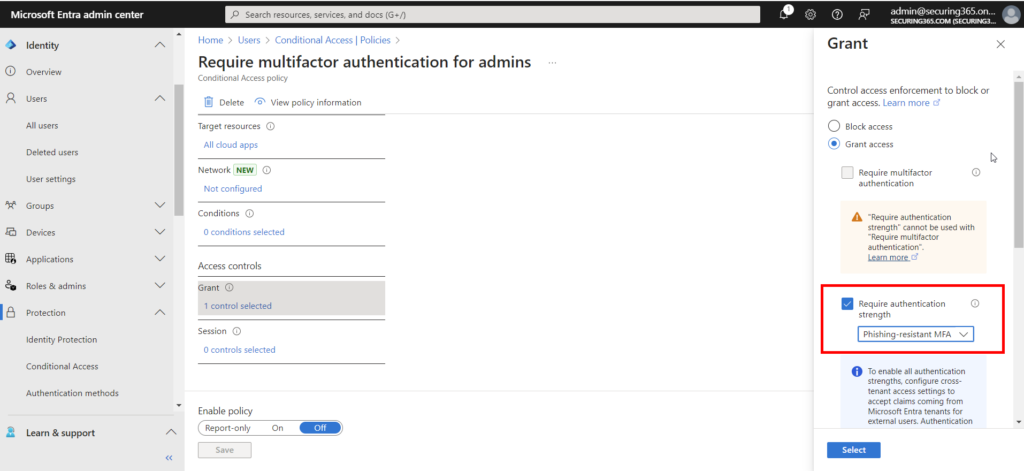
These keys cannot be hijacked like a session token granted with an app. This does require a FIDO security key to be added as an authentication method for the users targeted by this policy PRIOR to enforcing. If you are interested in deploying FIDO security keys to your users, read more here!
Conclusion
In conclusion, implementing MFA for administrative accounts is critical step in safeguarding your organization’s most critical assets. Administrative accounts hold the keys to the kingdom, and without proper controls, these accounts are prime targets for attackers. By enforcing MFA, you add a vital layer of defense that significantly reduces the risk of unauthorized access, even if credentials are compromised.
It’s important to remember that MFA is not a one-size-fits-all solution. It should be part of a broader, multi-layered security strategy that includes regular monitoring, security awareness training, and the use of advanced tools to detect and respond to threats. Ultimately, the goal is to make it as difficult as possible for attackers to gain access to your administrative accounts, ensuring that your organization remains secure in an increasingly hostile digital landscape.
References:

