Microsoft Defender for Endpoint (MDE) provides advanced threat protection for your Linux workloads, including linux-based instances. If you need to manually onboard a Debian server to MDE, follow this straightforward guide to get up and running in no time.
Prerequisites
A valid Microsoft Defender for Endpoint subscription
- Access to the Microsoft Defender Security Center (security.microsoft.com)
- A Debian-based system (our system is Debian 12)
- Root or sudo privileges on the system
- Internet access to download required packages and communicate with Defender services
- Putty
- WinSCP
Step 1: Download the Onboarding Package
- Sign in to Microsoft Defender Security Center.
- Navigate to Settings > Endpoints > Onboarding.
- Select Linux as the operating system.
- Select Streamlined as the connectivity type.
- Select Local Script (python) as the Deployment method.
- Download the
zipfile for manual onboarding. - Extract the zip and hold onto the .py file
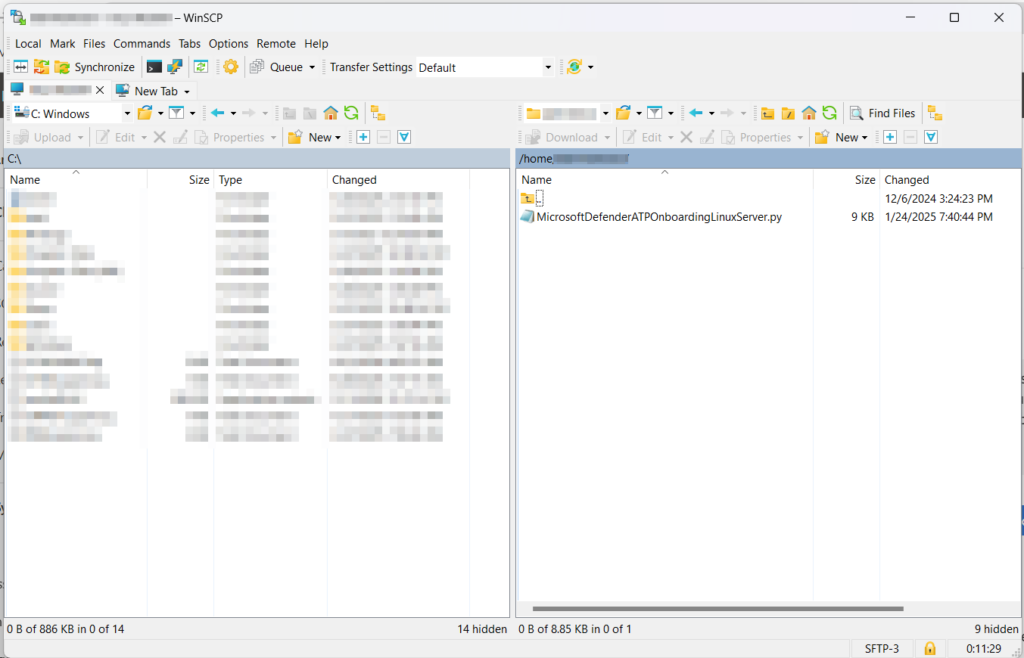
- Sign into your Debian server from WinSCP
- Transfer the file you extracted earlier to the Debian server
Step 2: Install Microsoft Defender for Endpoint
Run the following commands to install prerequisites: (you may need to elevate to sudo by using “su”)
curl -o /etc/apt/sources.list.d/microsoft-prod.list https://packages.microsoft.com/config/debian/12/prod.list
curl -sSL https://packages.microsoft.com/keys/microsoft.asc | gpg --dearmor | sudo tee /usr/share/keyrings/microsoft-prod.gpg > /dev/nullNow we can install MDE itself:
apt clean && apt autoclean && apt update && apt install mdatpNow we can get the MDE installer script from Microsoft’s Github repository:
wget https://raw.githubusercontent.com/microsoft/mdatp-xplat/refs/heads/master/linux/installation/mde_installer.sh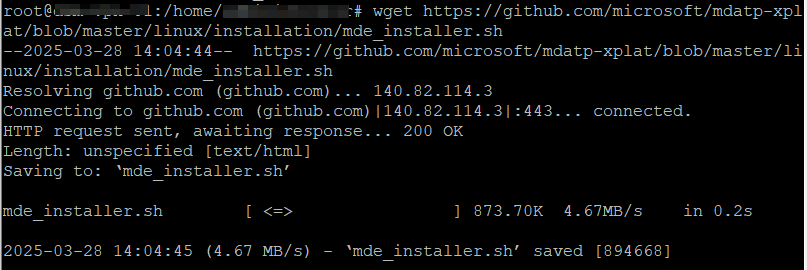
We need to grant permissions on the files we are using to make them executable:
chmod 755 mde_installer.sh MicrosoftDefenderATPOnboardingLinuxServer.pyAnd now we can run the installer script along with the onboarding specifications:
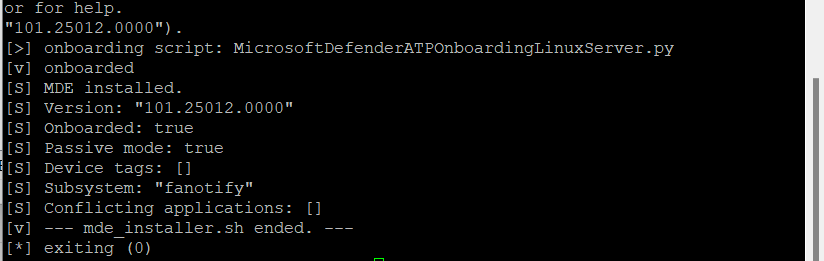
sudo ./mde_installer.sh -i -o MicrosoftDefenderATPOnboardingLinuxServer.pyAs long as we see Onboarded: “true” we are good to go!
We have one more step, make sure we have real time protection enabled!
sudo mdatp config real-time-protection --value enabled 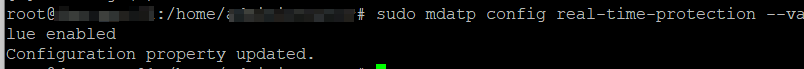
Step 3: Verify Installation
Check if the service is running and properly onboarded:
mdatp health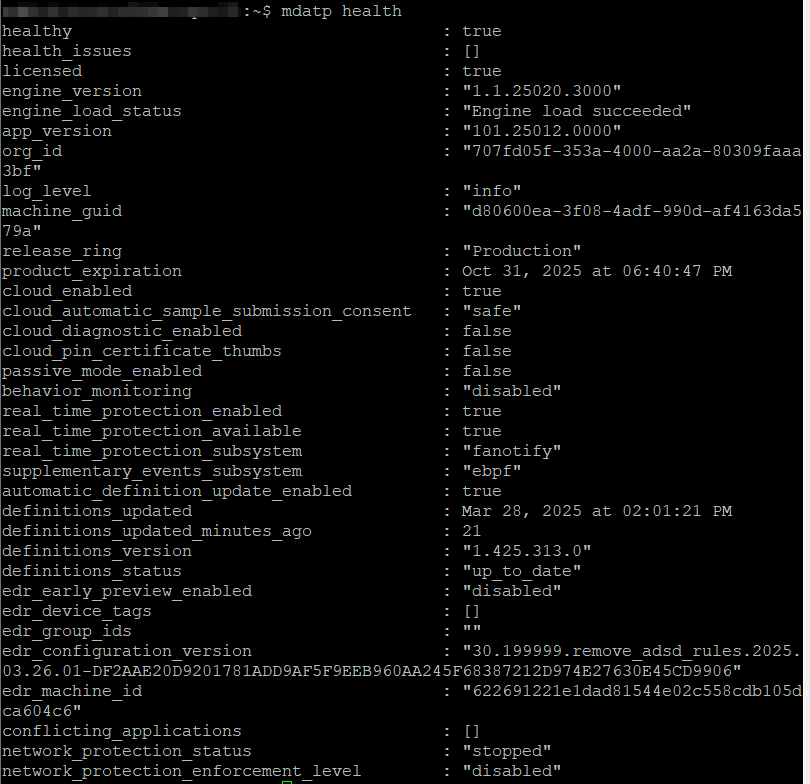
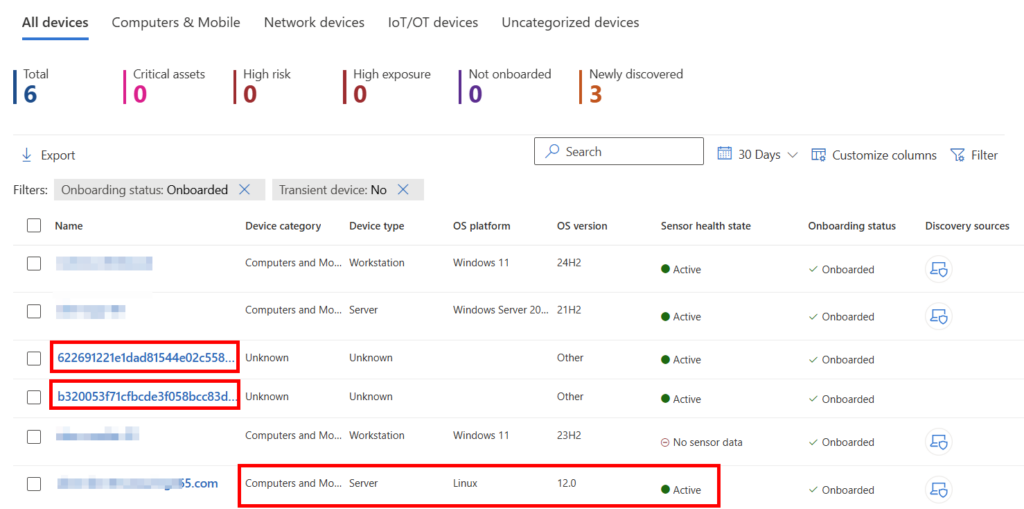
Step 4: Confirm Device is in the Defender Portal
Go back to Microsoft Defender Security Center, navigate to Assets > Devices, and confirm your Debian instance appears as onboarded. It may take a few hours for the device to show up. For example, our recently onboarded device is one of the GUIDs in the screenshot, whereas a device onboarded a few hours ago is listed below it.
Conclusion
Now we have a concise guide to onboarding Debian devices to Defender for Endpoint. Other Linux distros and flavors should be very similar, but may require some small adjustments to language. In the coming days I will try other Linux distros and will post an updated guide if those steps do require significant rework.
Stay secure and keep protecting your Linux workloads!


