RDP – the tool all sysadmins use, but also the tool and protocol that is targeted by threat actors the most. Protecting RDP and making sure it is only accessible by authorized personnel should be one of the highest priorities to most organizations. For those unaware, RDP is remote Desktop Protocol and is a tool to remotely manage Windows servers. Today we are going to talk about How To: Protect RDP with Microsoft Entra ID PIM and Entra Suite.
Why Secure RDP?
RDP is widely used for remote management and access, making it a common target for:
- Brute-force attacks
- Credential theft
- Man-in-the-middle attacks
Unsecured RDP access can lead to data breaches, ransomware infections, and significant business disruptions. Most organizations have RDP protected by their perimeter firewall and allow access to servers via RDP once you are on their trusted network. With most organizations having somewhat of a remote presence for employees, remote access is all the more important, but we do need to keep security in mind.
Prerequisites
To properly secure RDP using Entra ID PIM and Entra Suite, there are a few things that have to be implemented.
- Entra ID
- Entra ID (formerly Azure Active Directory) is the authentication mechanism for Microsoft 365. For this article, we have Entra ID already functioning and used by a few users.
- Entra ID Privileged Identity Management
- Entra ID PIM is the Just-In-Time access tool for Entra ID. Users can activate privileged roles using this tool. We will use PIM in this to grant access to a remote access group.
- Entra Suite / Global Secure Access
- Entra Suite is a collection of identity and access management tools from Microsoft that provides a unified platform for managing secure user access to both cloud and on-premises applications. We will be using Global Secure Access to connect to our on premises environment. Global Secure Access replaces your traditional end user VPN with an always on and secure connection to Microsoft’s datacenters, which also connect to your on premises environment via additional connectors.
Our Requirements
- Remove full network access for all users and only grant approved users access to our RDP resources
- Require only the approved users to utilize Just-In-Time permissions to access RDP
Our Network
- Entra ID P2 and Entra Suite are licensed in the tenant
- Private Connector Setup on a Windows 11 Machine in the on-premises network
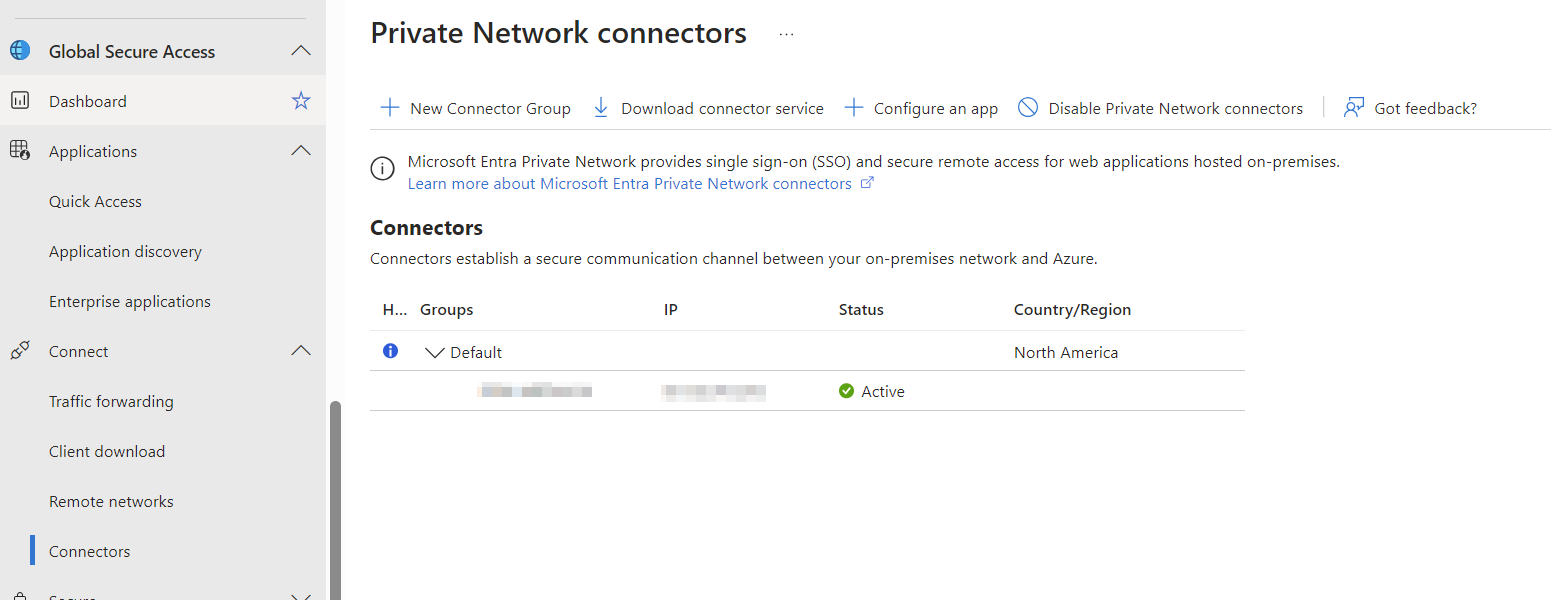
- Windows Server in the on-premises network with RDP open to only that network
Let’s get started
Our Security Group with PIM Enabled
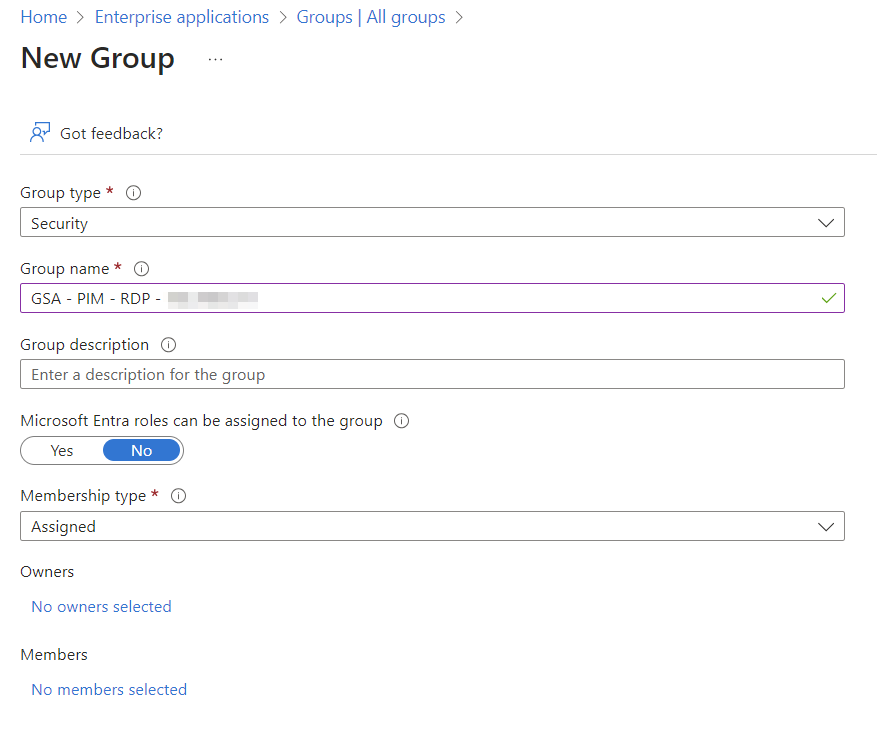
Let’s create a security group in Entra ID named: GSA – PIM – RDP – xxx.xxx.xxx.xxx
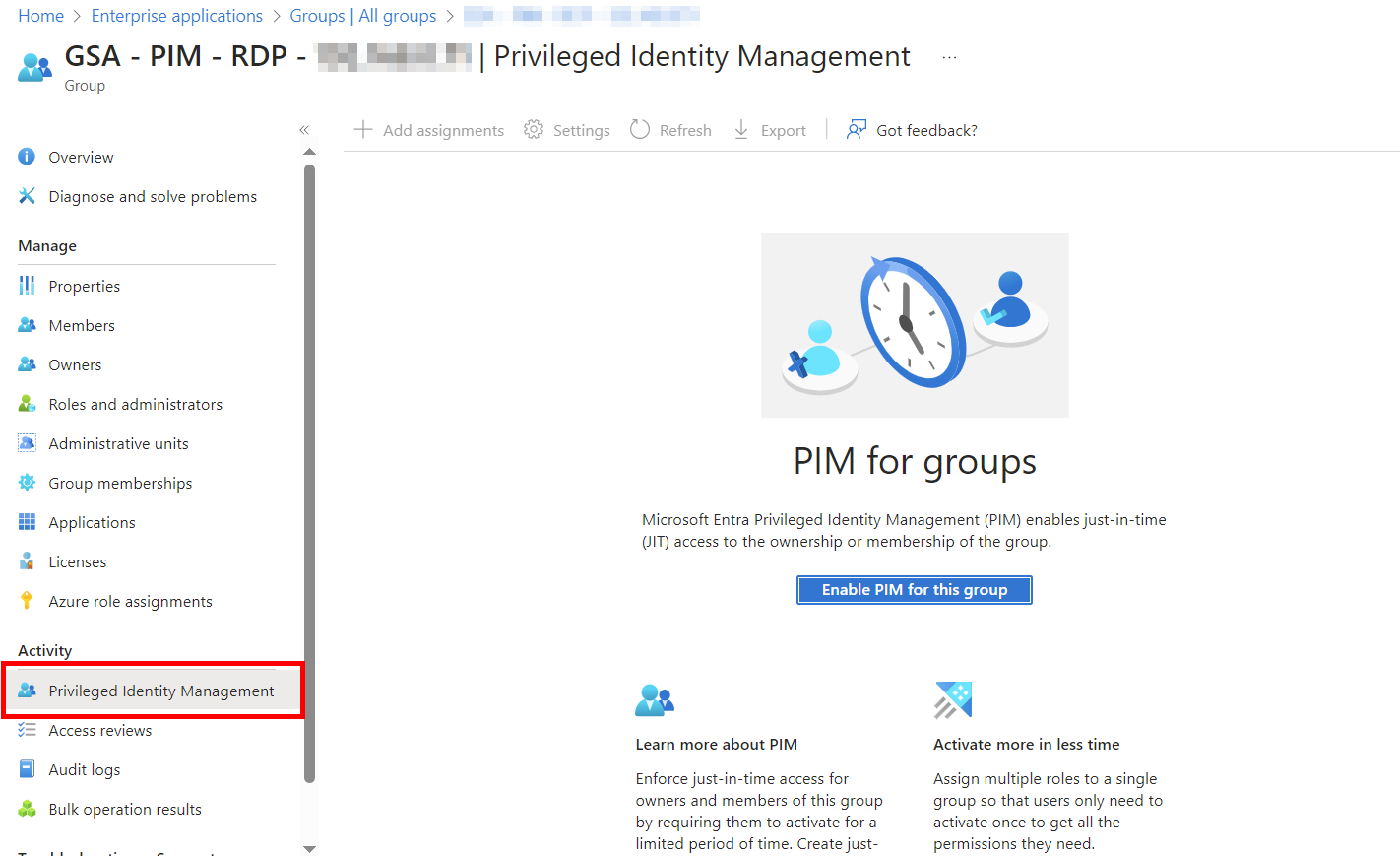
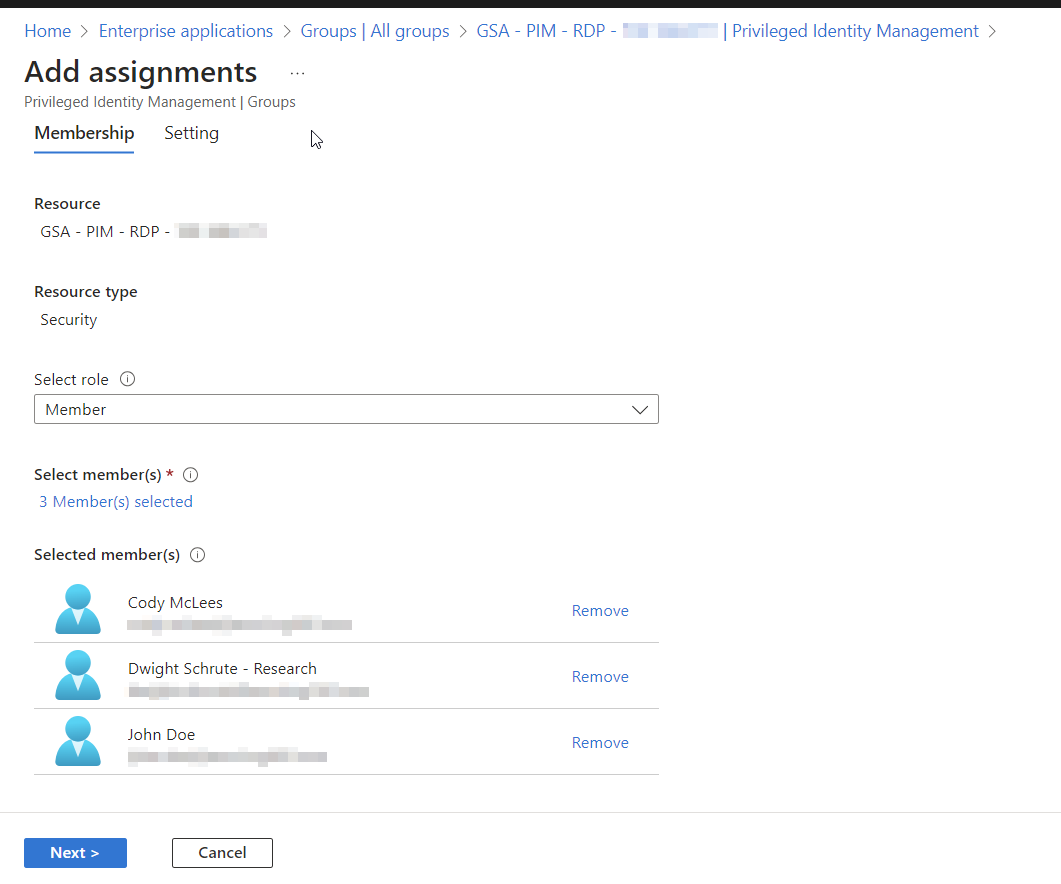
Enable PIM on this security group and make your approved staff eligible for access
Our Application to Allow These Users to RDP to our host
In Global Secure Access, Navigate to Enterprise Applications, and select new application:
Name your application: GSA – RDP – xxx.xxx.xxx.xxx
Connector Group: Default – leave this be unless you have made other adjustments
Enable Access with Global Secure Access Client: Leave this checked, that’s why we’re here!
Select “Add Application Segment” > Input the IP address of the destination host we want to grant access to. Port 3389 is used for RDP. Click Apply, then Save. We have another step after this, keep reading!
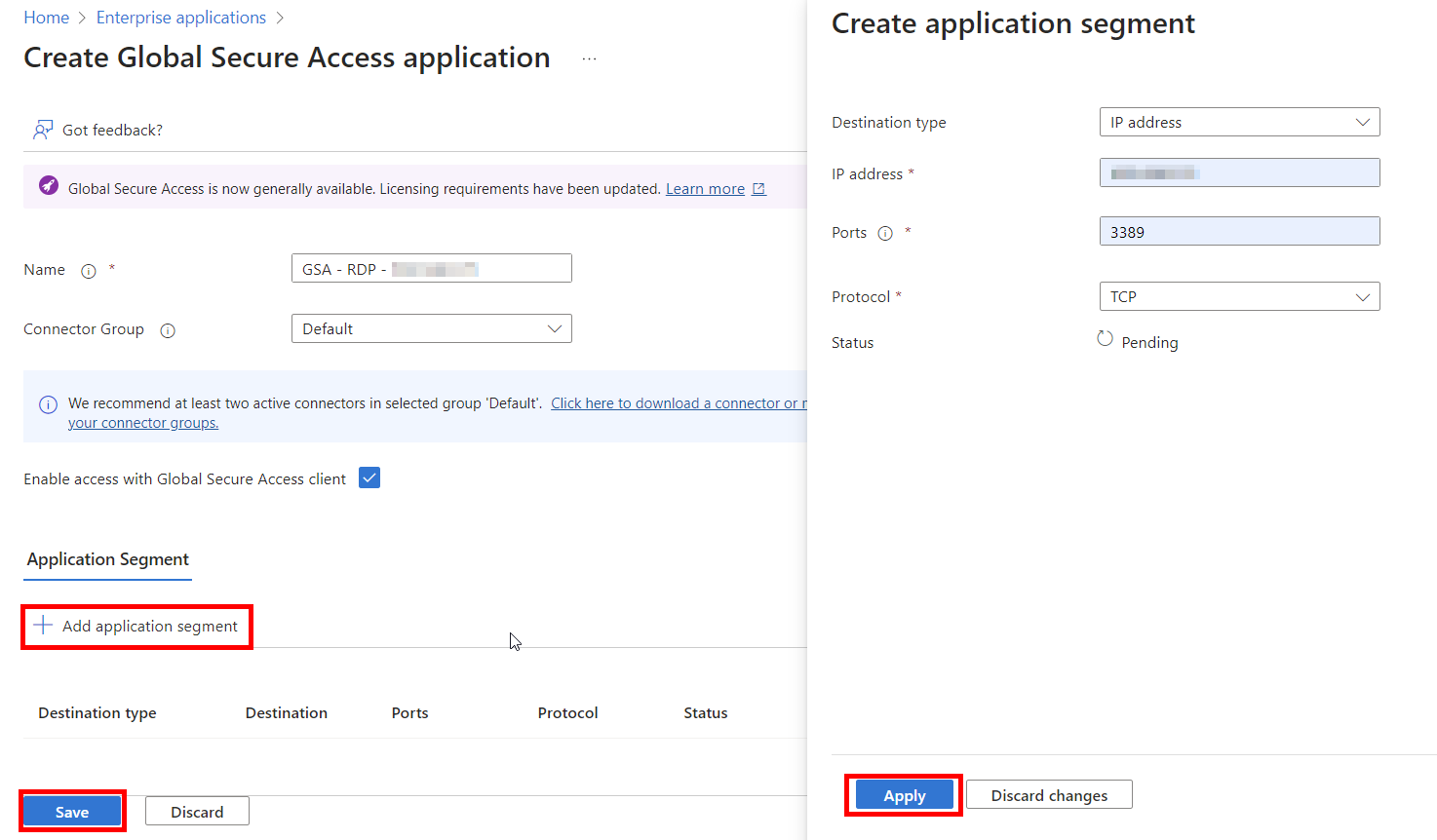
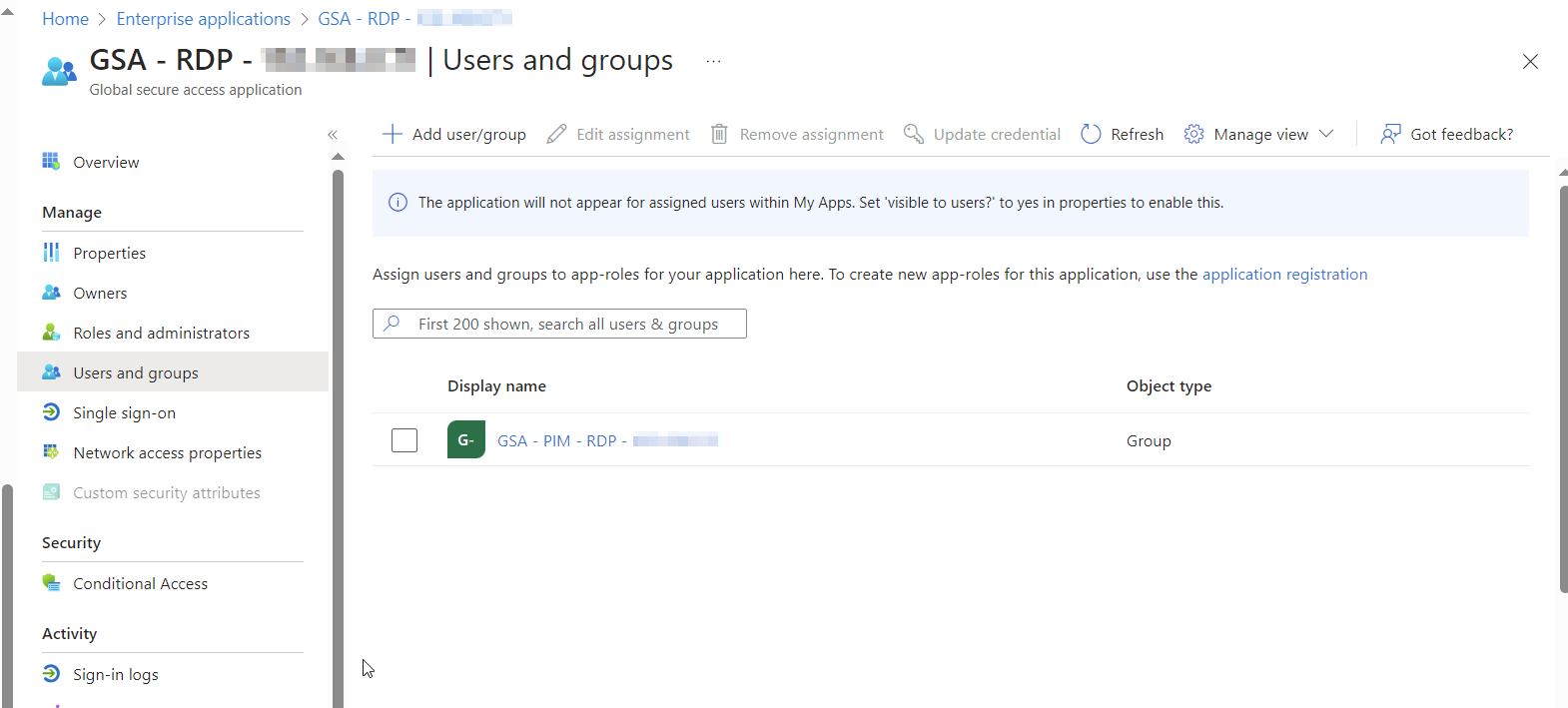
Next, we need to grant permission to our PIM security group. Go to your GSA Enterprise applications again, then select the app we just created. Once here, select the group we created earlier in this tutorial.
Let’s Test!
On our end user machine, we can see we are connected to Global Secure Access via the taskbar.
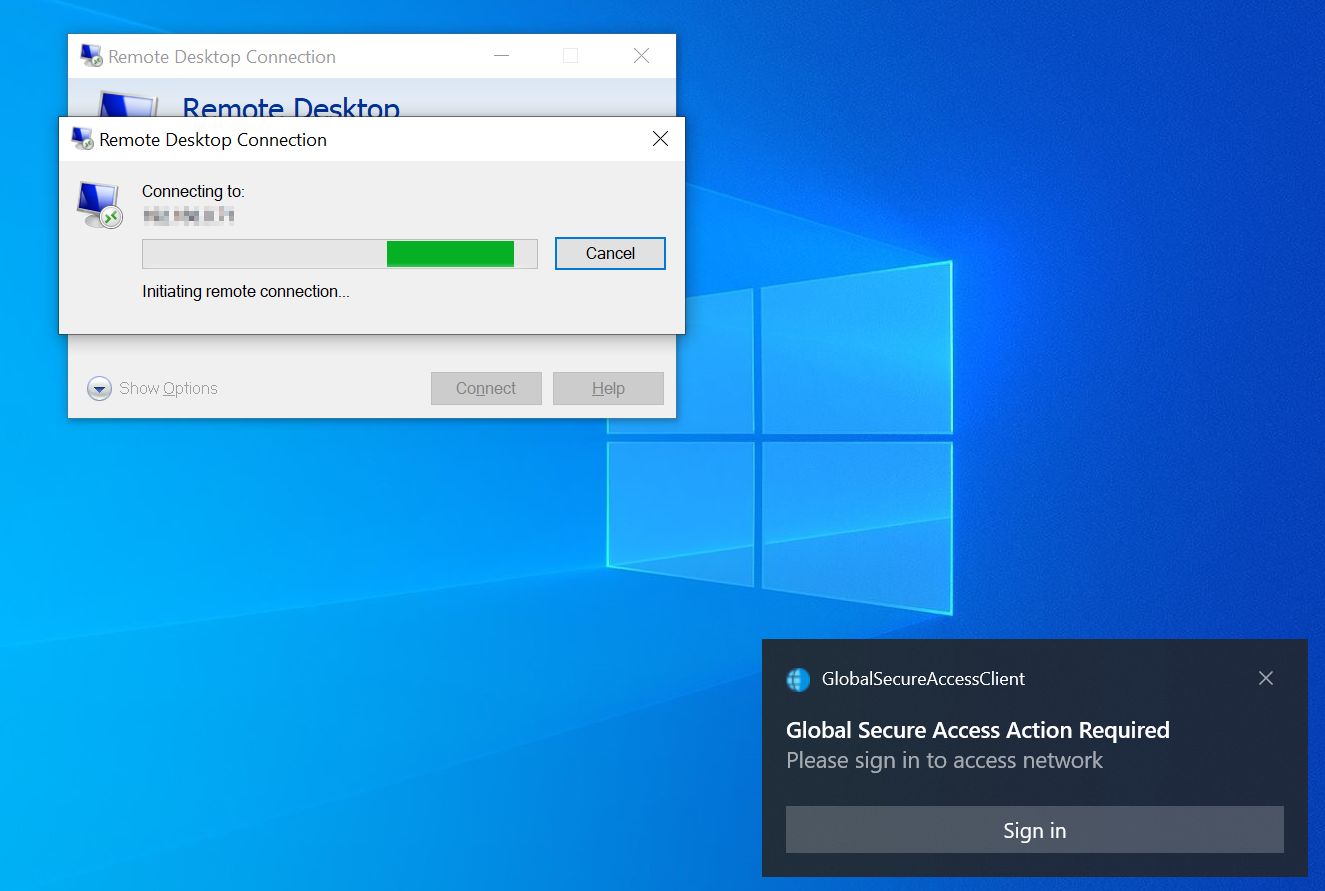
Now, let’s test to see if we can RDP to the server without using PIM.
When we try to connect, we get prompted with a window for GSA that tells us we need to sign in.
When we click sign in, we see that we aren’t a member of the group necessary to get to that resource and we aren’t allowed to connect.
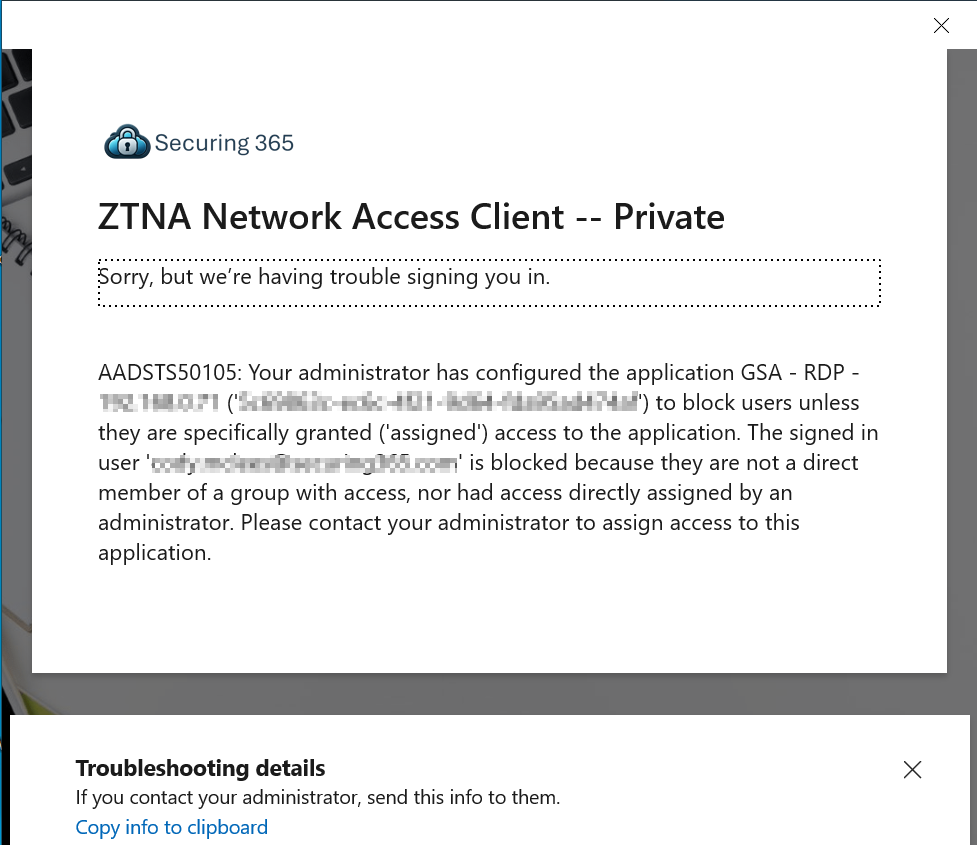
Now that we know our blocking and permissions work. Let’s have the user activate PIM for the security group, then have them attempt to sign in.
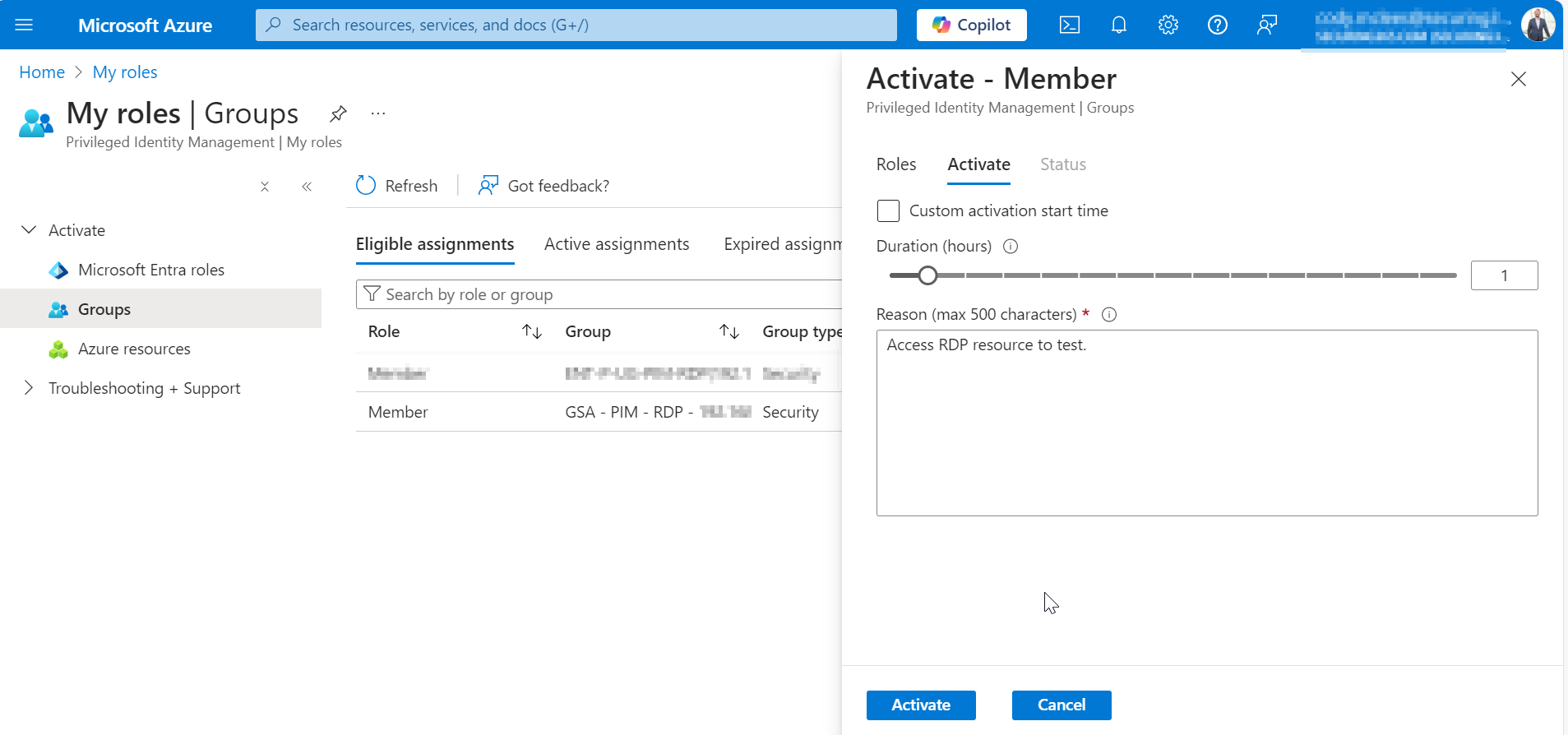
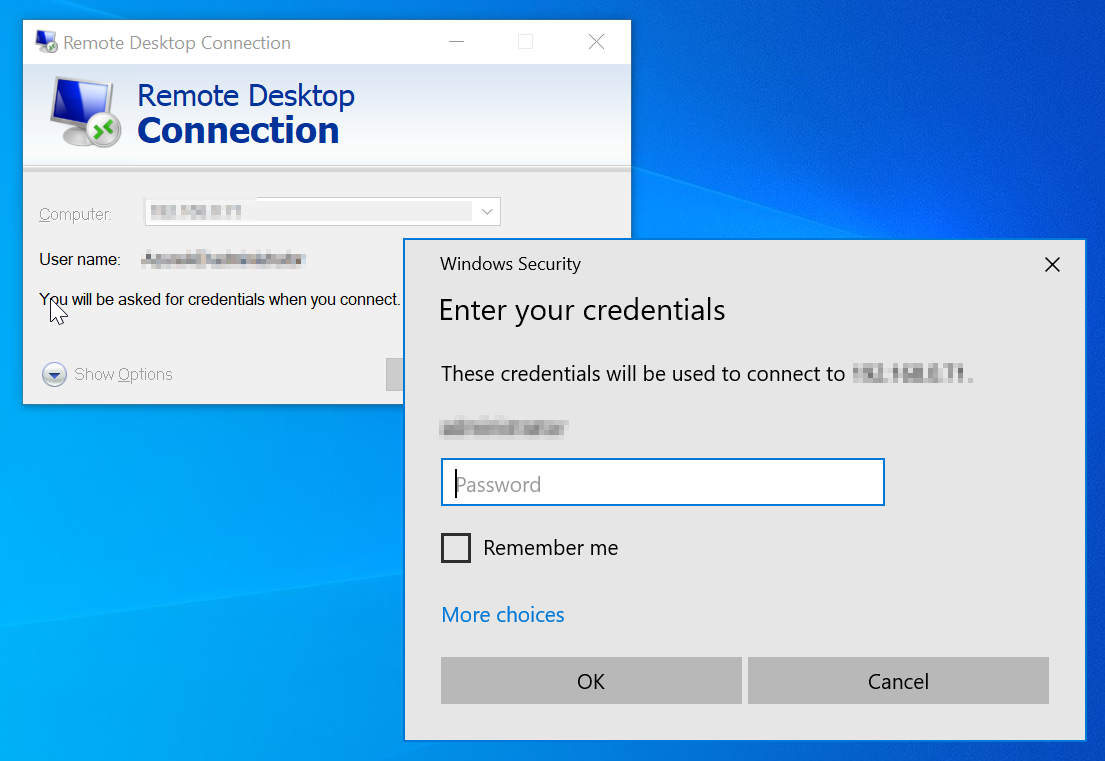
Once activated, the user can open Remote Desktop Connection, and attempt to connect to the RDP endpoint. Once we get to the window where credentials are requested, we know the connection works. We will follow through and sign in locally to showcase the sign in works.
Conclusion
Securing RDP is essential to maintaining a robust cybersecurity posture. By leveraging Microsoft Entra ID PIM and the Entra Suite, organizations can ensure secure, conditional, and controlled access to RDP environments. This layered approach minimizes attack surfaces, mitigates risks, and ensures compliance with security best practices.
Start protecting your RDP today with Microsoft Entra tools and safeguard your remote access infrastructure for the future.


