That’s right, in today’s post, I’m going to show you the free connectors you can get setup to ingest data and get started on Microsoft Sentinel. Follow along for more updates and more content like this!
What is Microsoft Sentinel?
Microsoft Sentinel is a scalable, cloud-native security information and event management (SIEM) solution that also incorporates security orchestration, automation, and response (SOAR) capabilities. It is designed to help organizations detect, investigate, and respond to cyberthreats across their entire enterprise. Think of it this way, if you have security logs from an appliance, application, device, etc – send them to Microsoft Sentinel and let it monitor and alert on correlated events.
What are the free connectors for Microsoft Sentinel?
The free connectors are a good starting point for adopting Microsoft Sentinel and getting a SEIM in place. The free connectors available can be found below or at this URL.
| Microsoft Sentinel data connector | Free data type |
|---|---|
| Azure Activity Logs | AzureActivity |
| Health monitoring for Microsoft Sentinel 1 | SentinelHealth |
| Microsoft Entra ID Protection | SecurityAlert (IPC) |
| Office 365 | OfficeActivity (SharePoint) |
| OfficeActivity (Exchange) | |
| OfficeActivity (Teams) | |
| Microsoft Defender for Cloud | SecurityAlert (Defender for Cloud) |
| Microsoft Defender for IoT | SecurityAlert (Defender for IoT) |
| Microsoft Defender XDR | SecurityIncident |
| SecurityAlert | |
| Microsoft Defender for Endpoint | SecurityAlert (MDATP) |
| Microsoft Defender for Identity | SecurityAlert (AATP) |
| Microsoft Defender for Cloud Apps | SecurityAlert (Defender for Cloud Apps) |
Let’s Set Sentinel Up with the Free Connectors
Prerequisite: Setup an Azure Subscription
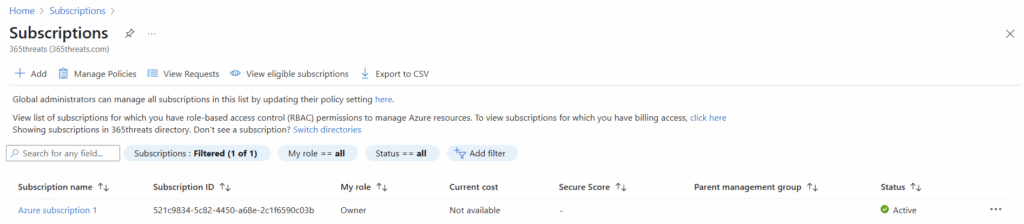
Since this environment doesn’t have any subscriptions, we are going to setup a subscription. Since this is the first subscription in this tenant, I’m eligible for a free trial that I will setup.
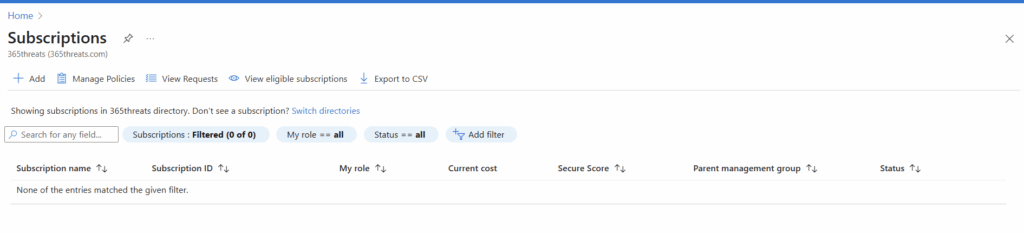
After signup of the trial (you do have to give them a credit card), I now have a subscription where we can get setup with Sentinel.
Let’s Setup a Log Analytics Workspace
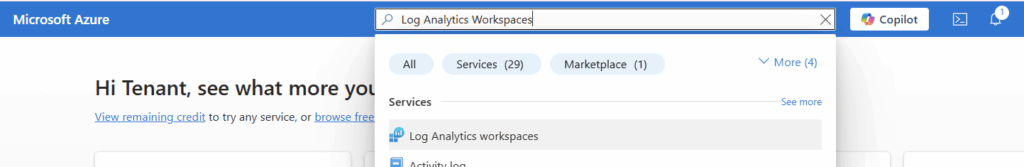
First, we need a workspace for the logs to land in. In the blue search bar at the top, we can search for Log Analytics Workspaces.
We can create a workspace here.
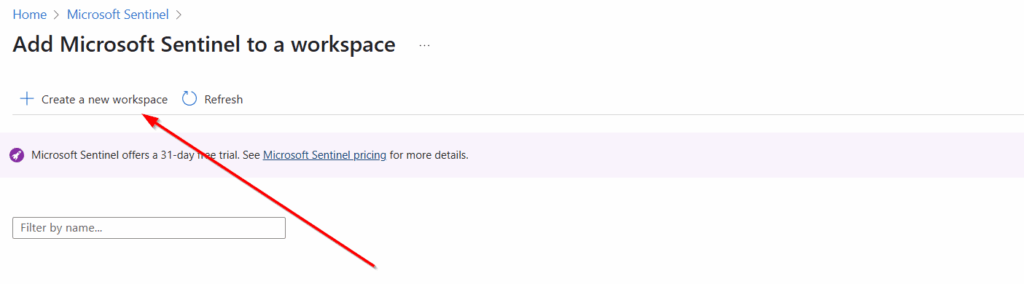
Because we are in a net new environment, we will also need to create a resource group. As you can see in the below screenshot, I called mine Sentinel-RG. In the name for the Log Analytics workspace, I called it LA-Sentinel.
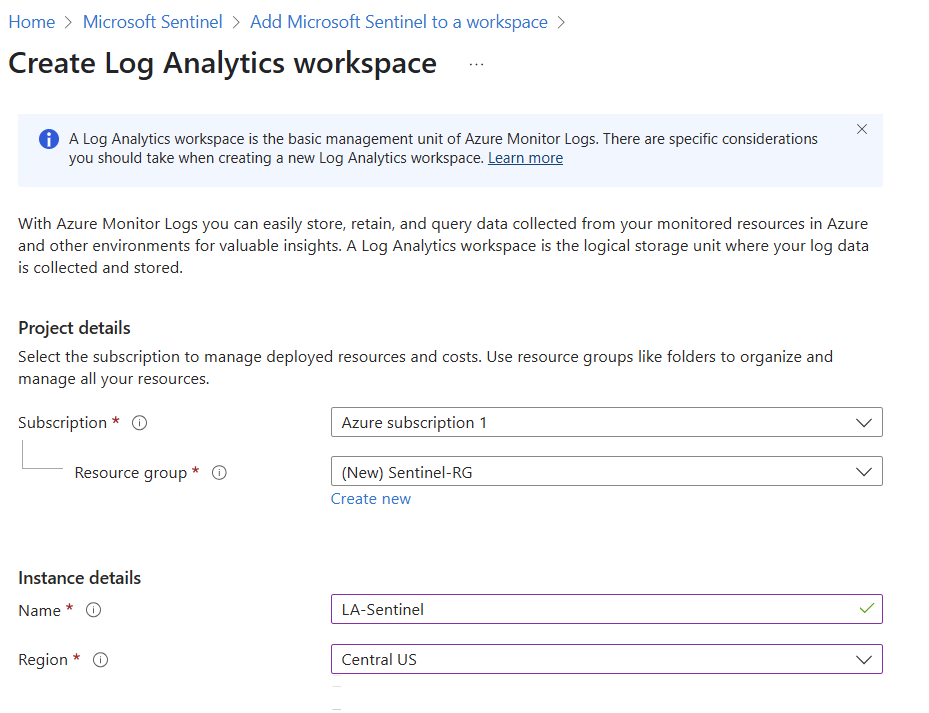
Once our Analytics Workspace is created, we will be taken to a page that shows our deployment is complete.
Let’s Setup Sentinel
In the blue search bar at the top of the Azure portal, we will search for Sentinel.
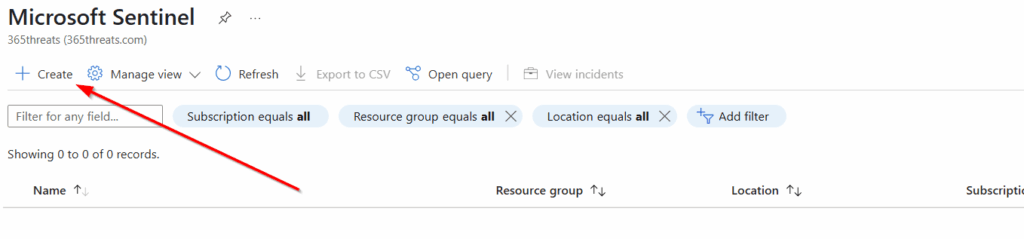
In Sentinel, we will select create.
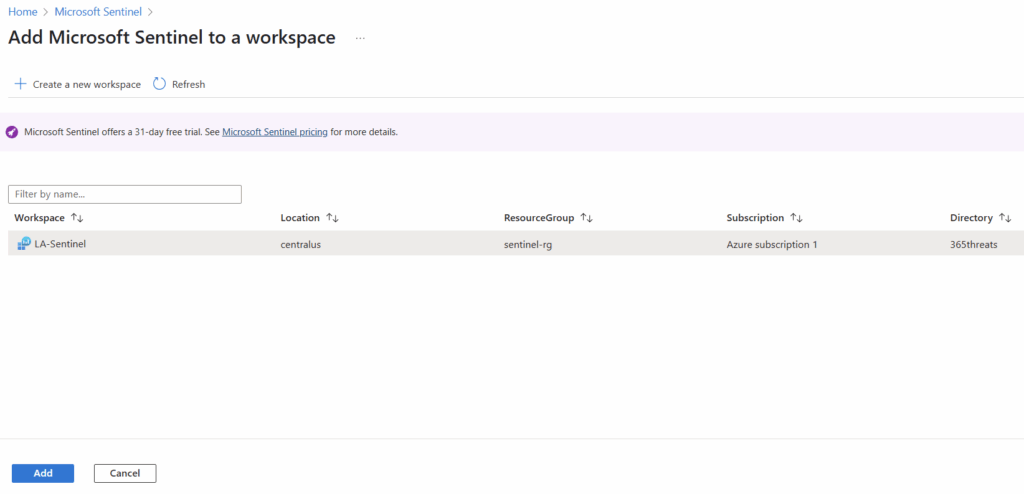
We will select the Log Analytics Workspace we just created and click “Add.”
It will take a minute or two, but once complete, Sentinel will bring you to this page. We want to go to the “Content Hub” and setup our free connectors. You can use either of the links in the screenshot below to get to the Content Hub.
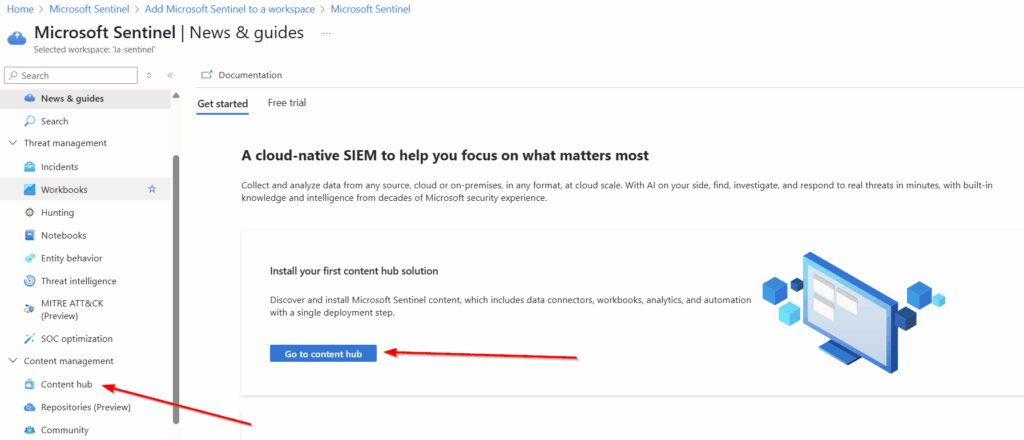
Let’s Setup our free connectors
Expand each section below for the step by step directions:
Azure Activity Logs
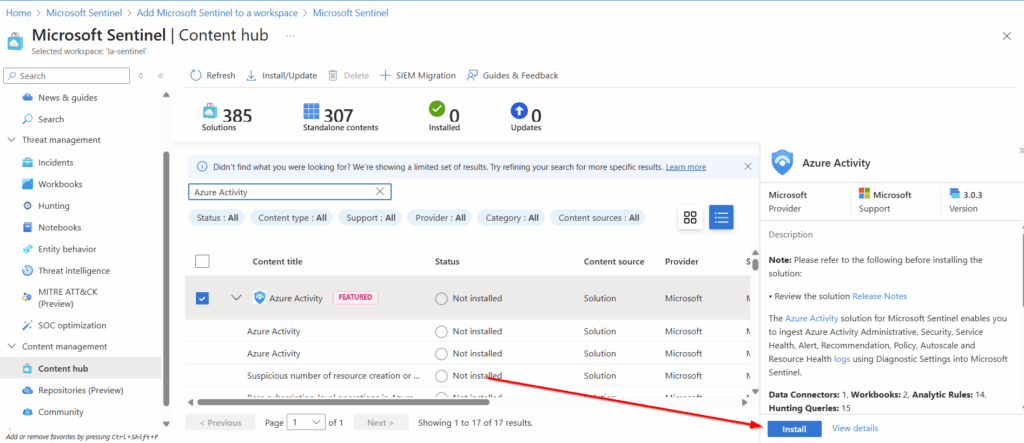
Using the search function in the Content Hub, we can find Azure Activity and select Install in the bottom right corner.
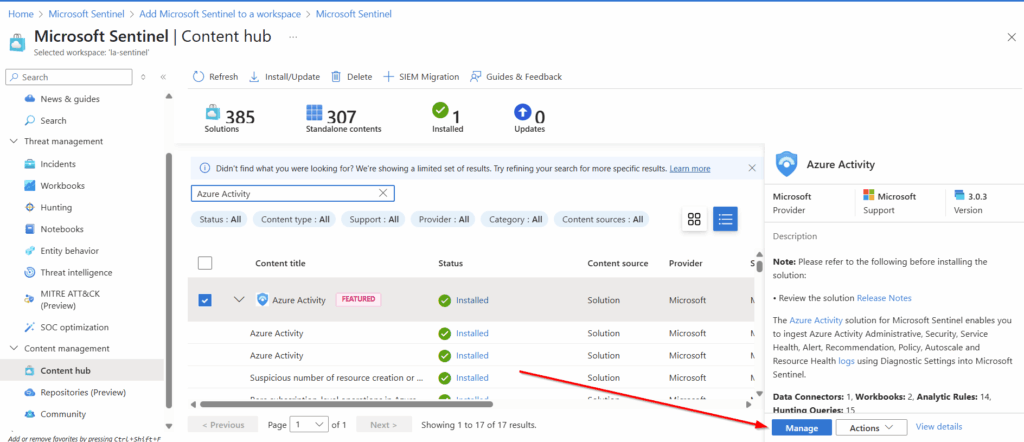
Once installed, select manage in the bottom right corner.
The specific connector we are looking for is also called “Azure Activity.” We will select it at the very top of the next page and will select “Open Connector page” in the bottom right.
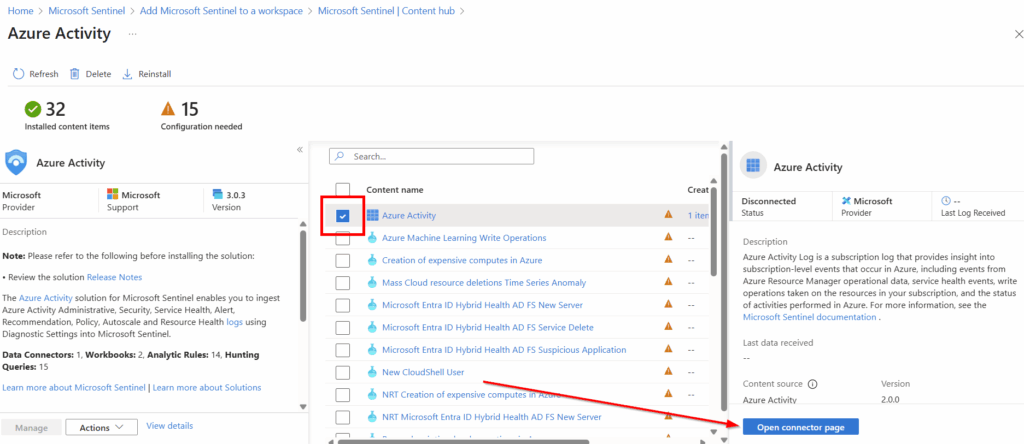
Within the connector we will get directed to Azure Policy Assignment wizard so we can tell all subscriptions to send their activity data to Sentinel.
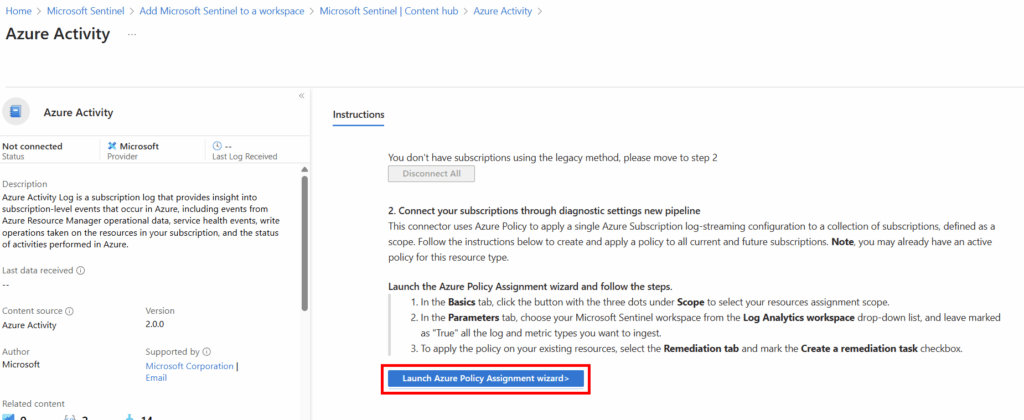
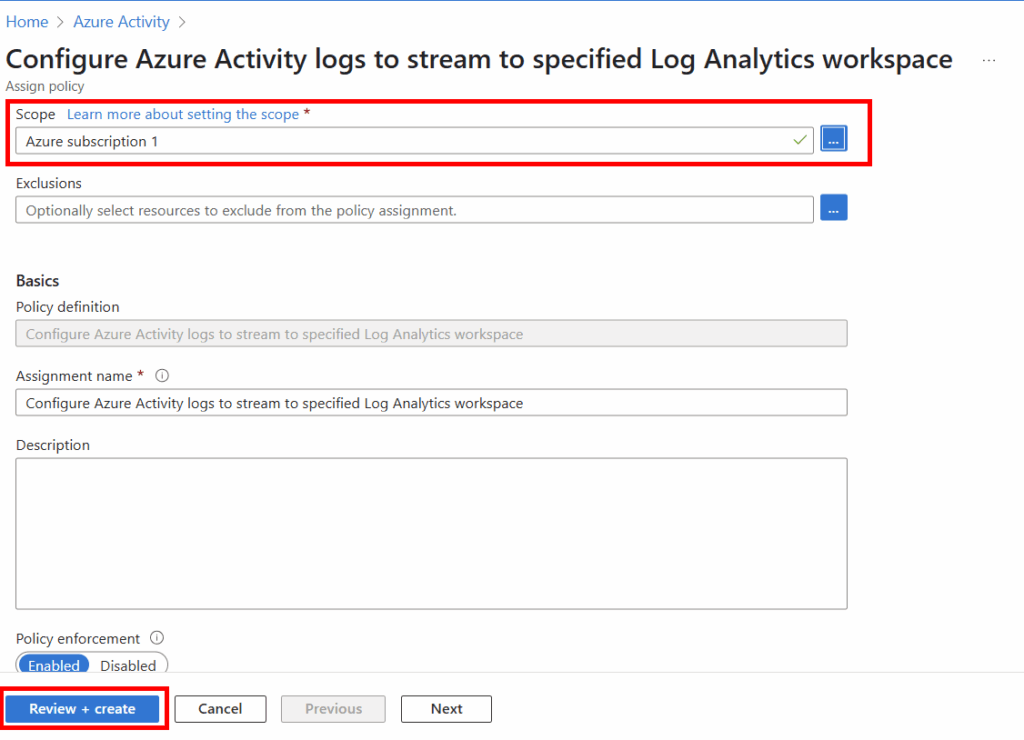
Within the Azure Activity Policy, the page will have most of the relevant information already selected, except for the subscriptions we want to target. You’ll want to select all of your applicable subscriptions, in my instance I only have one, so that is selected.
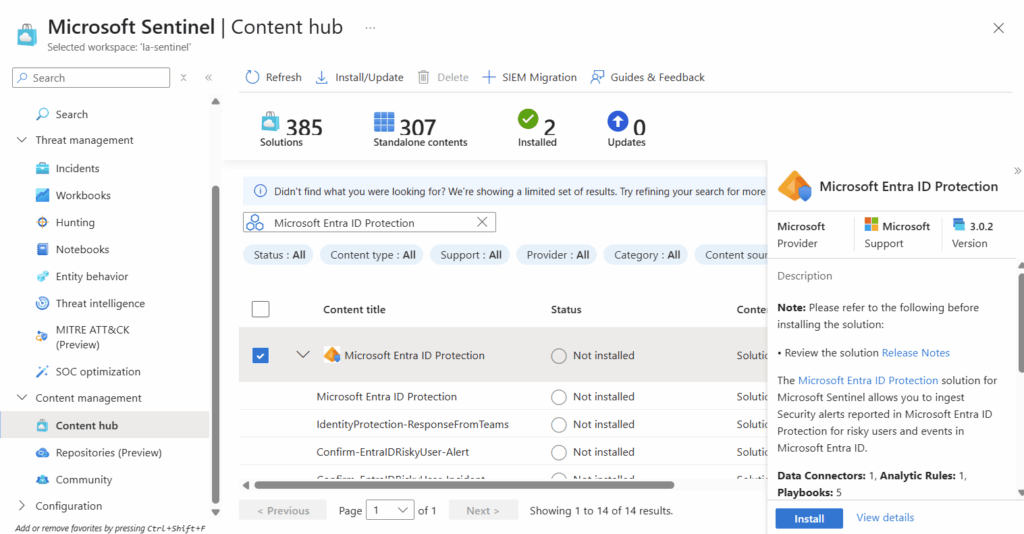
Microsoft Entra ID Protection
Using the search function in the Content Hub, we can find Microsoft Entra ID Protection and select Install in the bottom right corner.
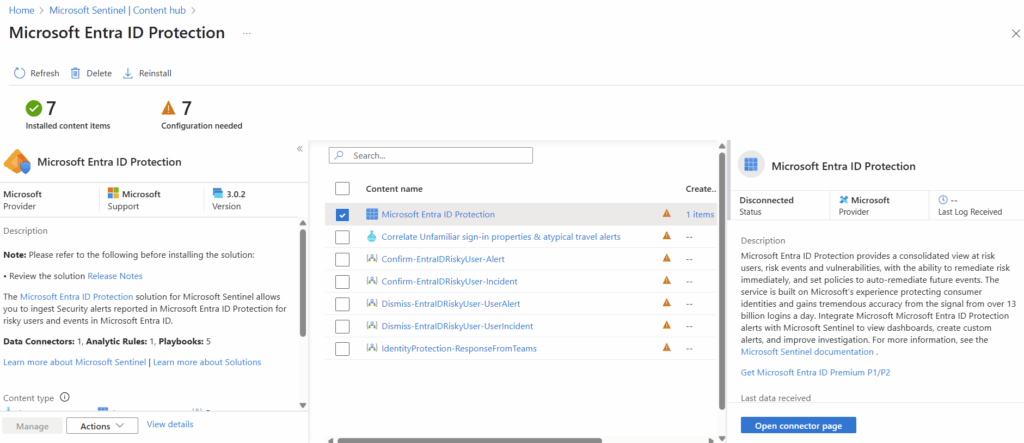
Once installed, select manage in the bottom right corner.
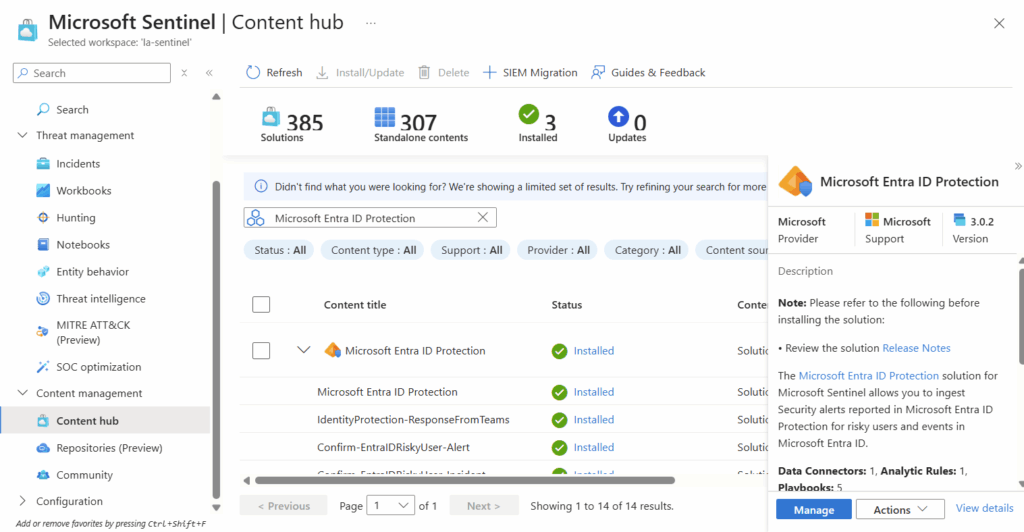
The specific connector we are looking for is also called “Microsoft Entra ID Protection.” We will select it at the very top of the next page and will select “Open Connector page” in the bottom right.
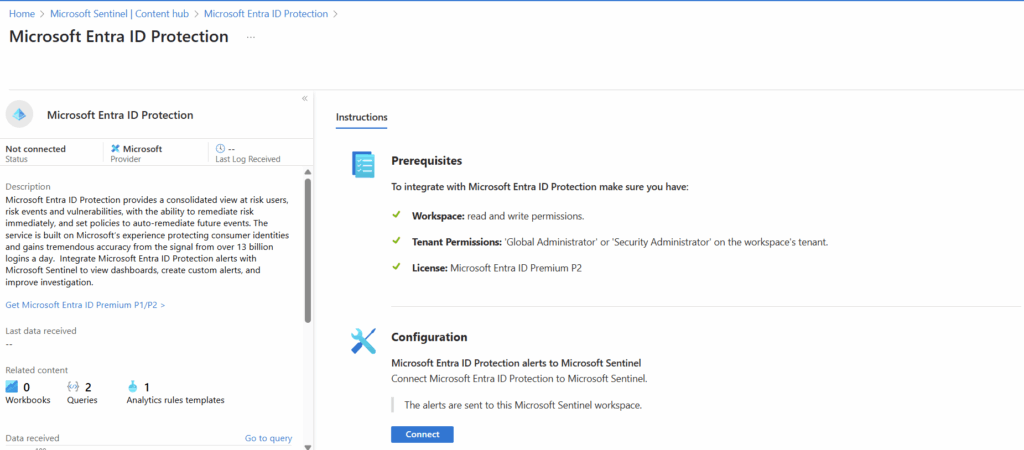
On the instructions page, we will select “Connect” which will be toward the bottom of the page.
Shortly after clicking connect, you should get a notification in the upper right that it was successfully connected:

Office 365
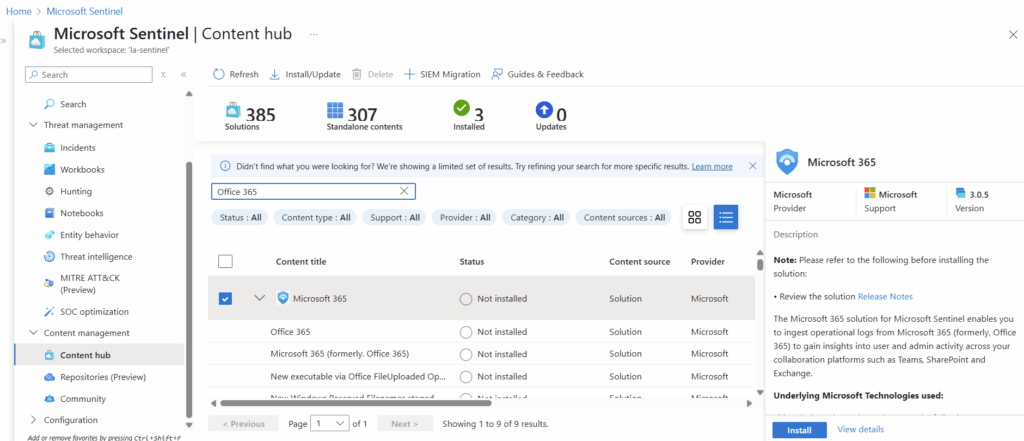
Using the search function in the Content Hub, we can find Microsoft 365 and select Install in the bottom right corner.
Once installed, select manage in the bottom right corner.
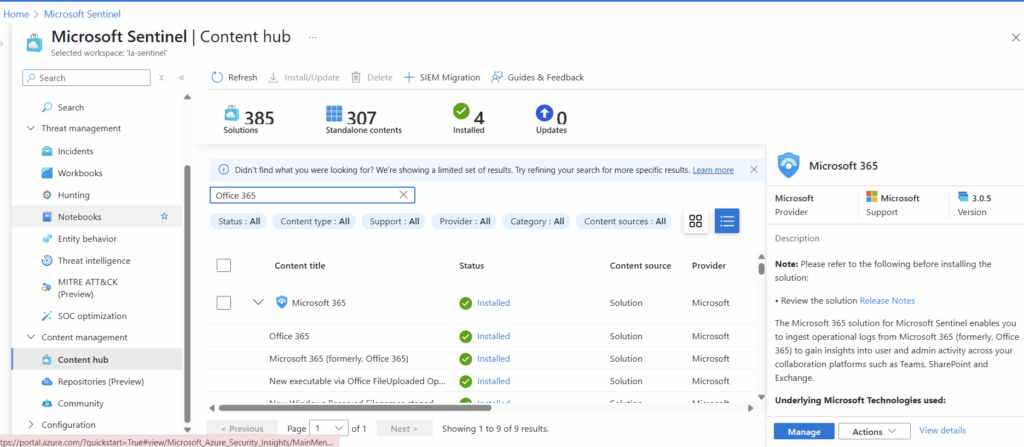
The specific connector we are looking for is also called “Microsoft 365 (formerly, Office 365).” We will select it at the very top of the next page and will select “Open Connector page” in the bottom right.
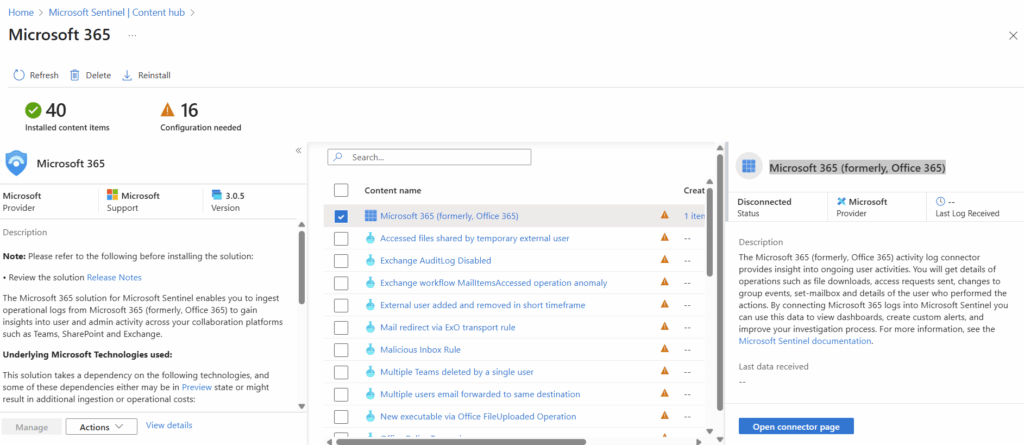
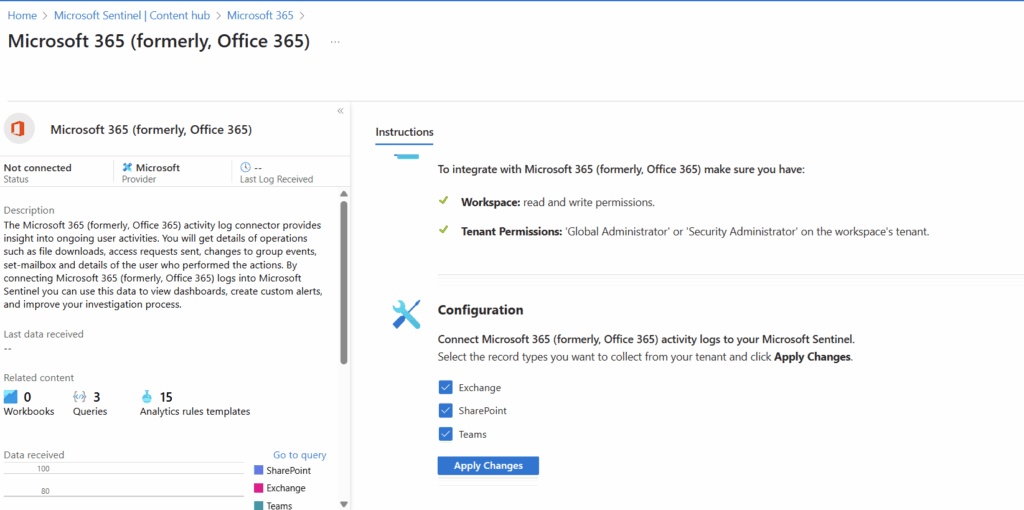
On the instructions page, we will select the checkboxes for Exchange, SharePoint, and Teams. Then we will select “Apply Changes.”
Microsoft Defender for Cloud
Using the search function in the Content Hub, we can find Microsoft Defender for Cloud and select Install in the bottom right corner.
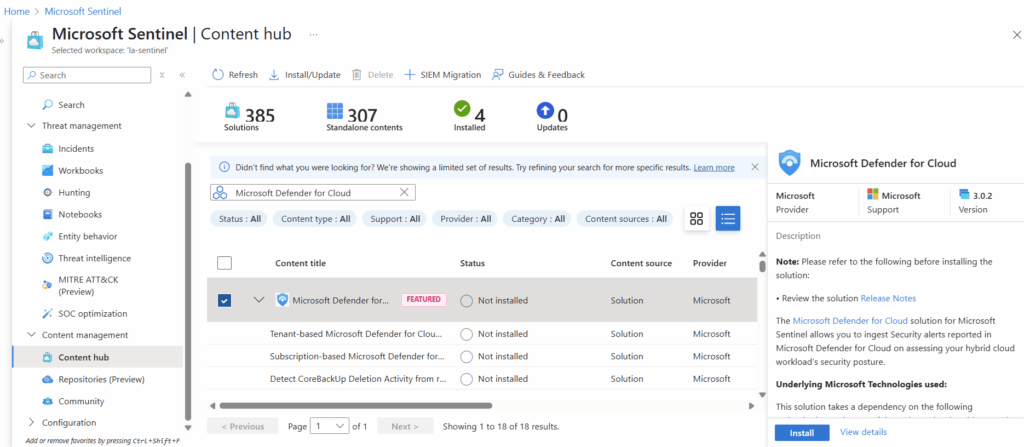
Once installed, select manage in the bottom right corner.
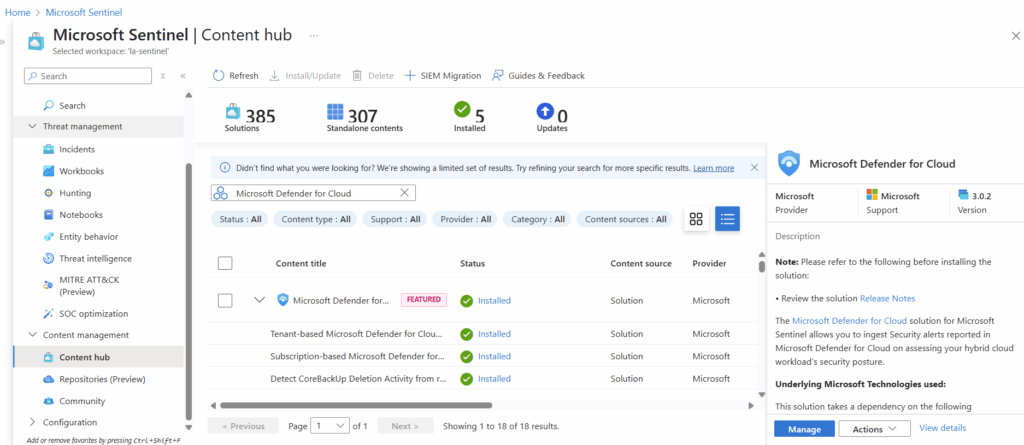
The specific connectors we are looking for are called “Subscription-based Microsoft Defender for Cloud (Legacy)” and “Tenant-based Microsoft Defender for Cloud (Preview).” We will select one of them at a time and select “Open Connector page” in the bottom right. At the time of writing of this article we had issues with getting the preview option configured and were unable to proceed so we configured just the legacy option.
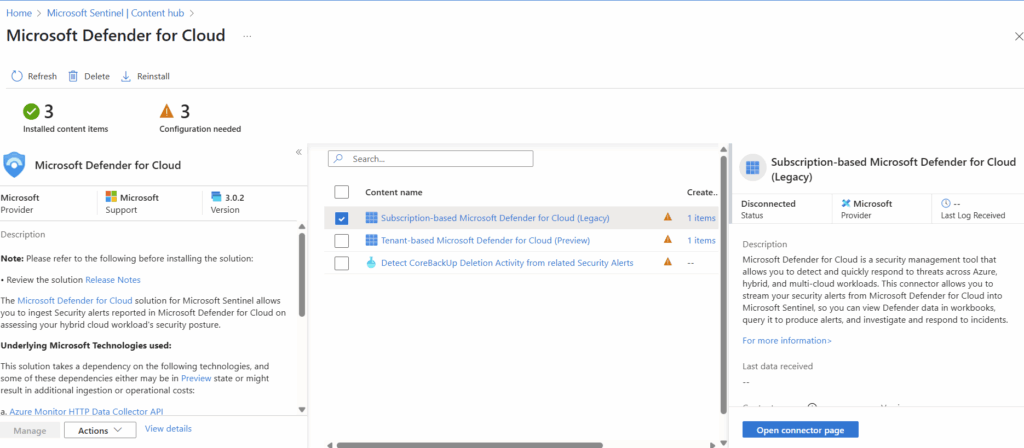
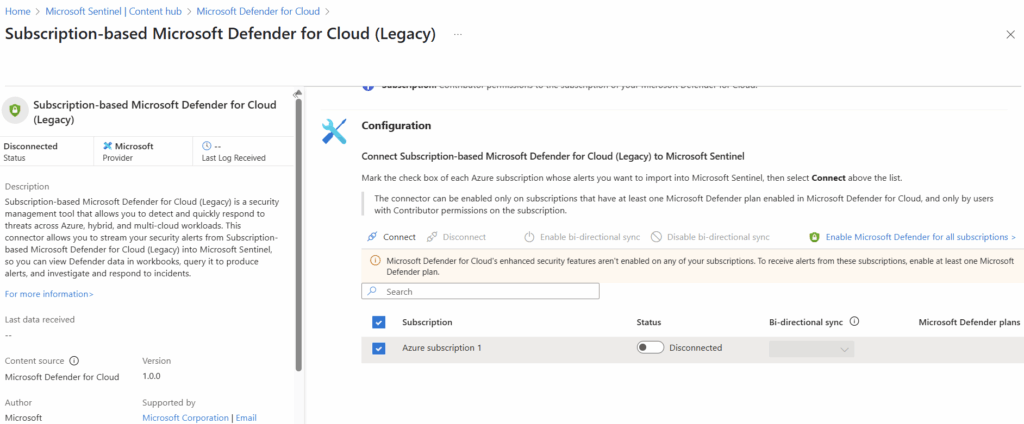
In the configuration page, we will select the checkbox next to our applicable subscriptions, then select connect to connect our subscriptions to Sentinel.
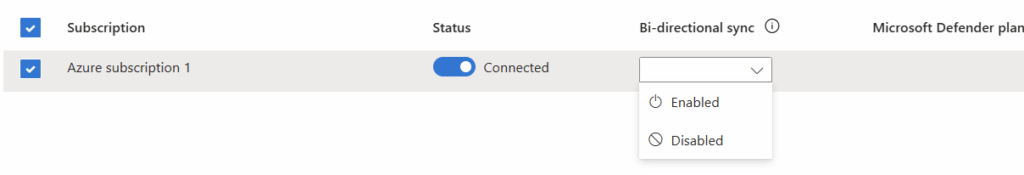
We will also enable bidirectional sync which will stream all Defender XDR incidents and advanced hunting events into Microsoft Sentinel and keep the incidents and events synchronized between the Azure and Microsoft Defender portals.
Microsoft Defender for IoT
Using the search function in the Content Hub, we can find Microsoft Defender for IoT and select Install in the bottom right corner.
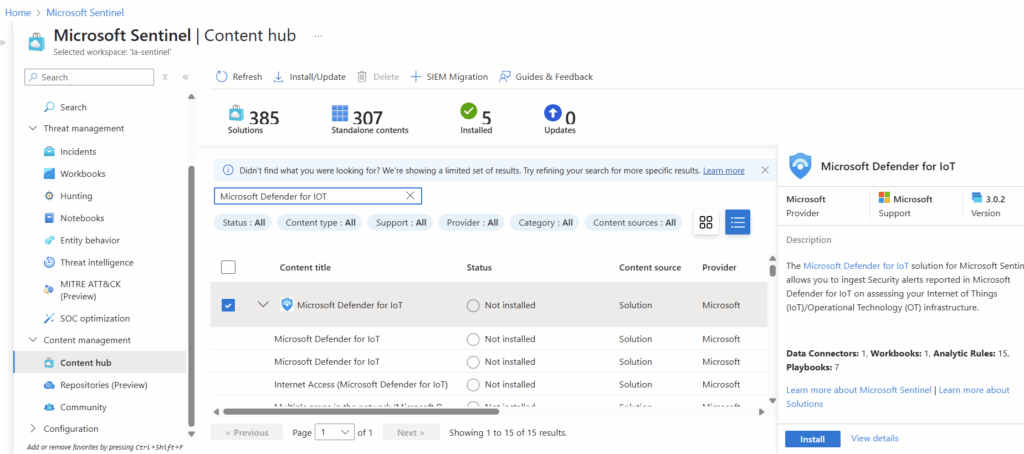
The specific connector we are looking for is also called “Microsoft Defender for IoT.” We will select it at the very top of the next page and will select “Open Connector page” in the bottom right.
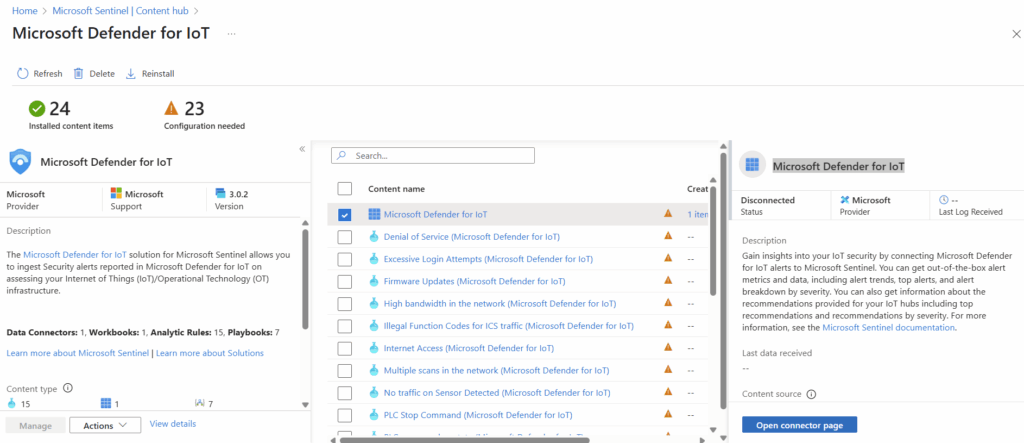
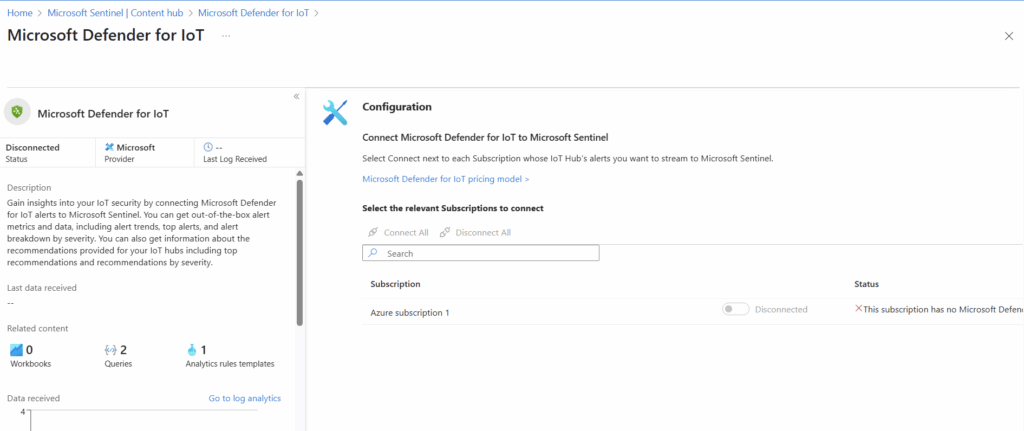
Now in our instance we don’t have any usage or hubs associated with Defender for IOT so it isn’t possible to connect to Sentinel. If we did, we would be able to select “Connect All” in the configuration page.
Microsoft Defender XDR
Using the search function in the Content Hub, we can find Microsoft Defender XDR and select Install in the bottom right corner.
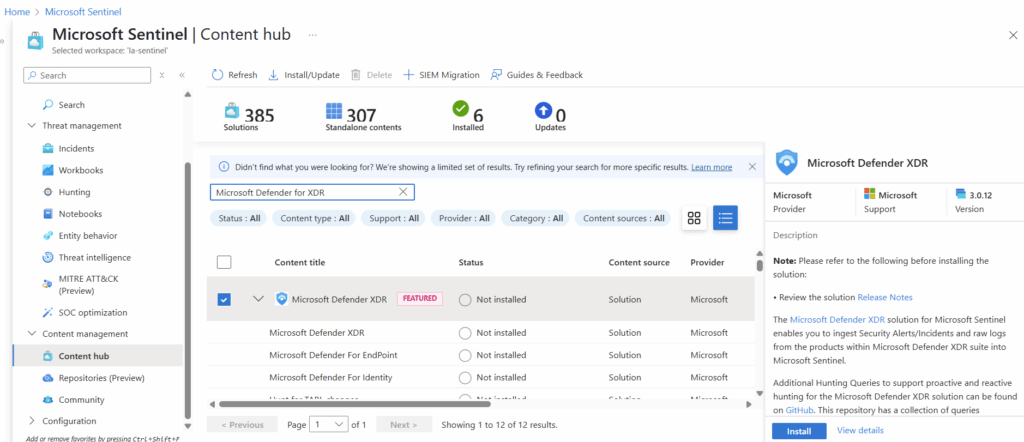
Once installed, select manage in the bottom right corner.
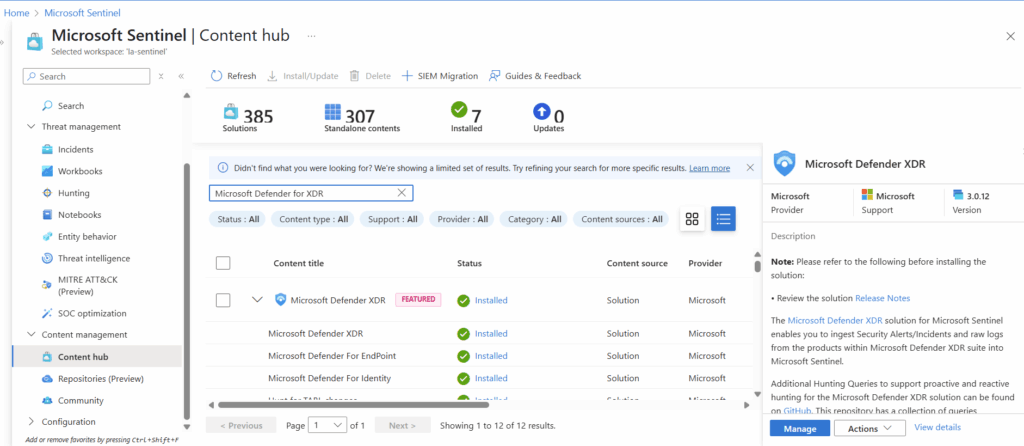
The specific connector we are looking for is also called “Microsoft Defender XDR.” We will select it at the very top of the next page and will select “Open Connector page” in the bottom right.
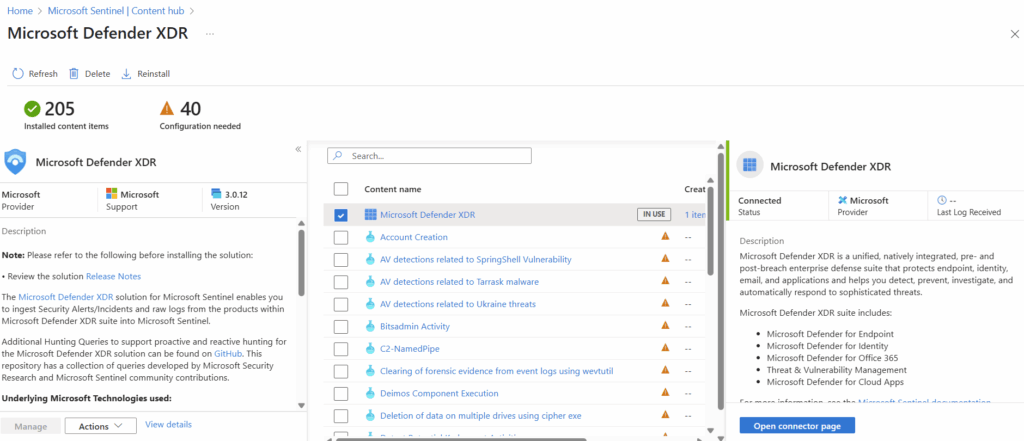
Now here is an important step/error you may run into. When trying to access the Defender XDR portal, I get what appears to be a Conditional Access message requiring a compliant device to sign in. I’m already on a compliant device, so something is wrong.
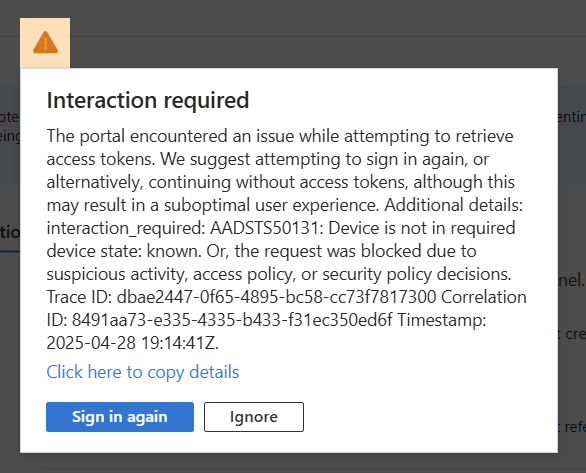
Trying to ignore or sign in again are futile, it feels like I cannot go any further. The fix is odd, but works. There was a classic conditional access policy added when we added this connector. Having run into this before, it took many hours to find this and can easily be removed without issue.
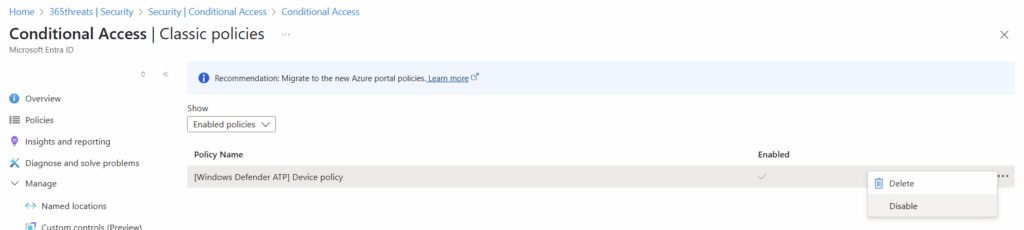
Now we can return to the Defender XDR connector and select “Connect incidents & alerts”
We can also go to https://security.microsoft.com/ and connect our Sentinel Workspace to our Defender Portal. This will change the look and feel slightly and ensure our free connectors are onboarded properly.
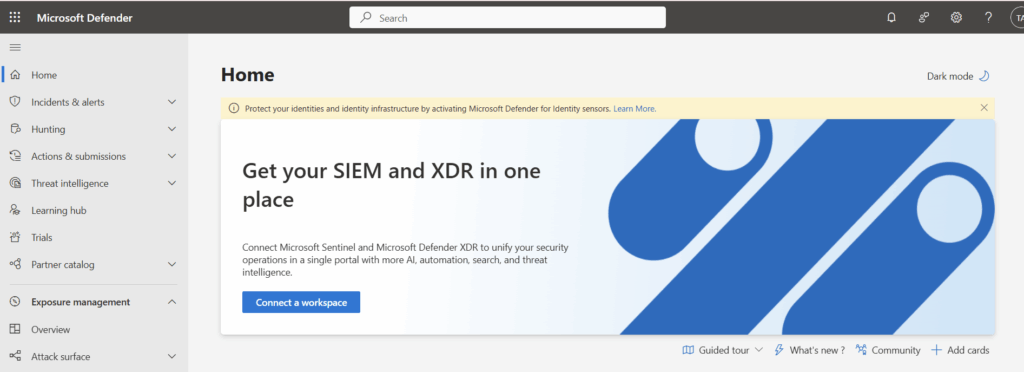
We will select the workspace we created at the beginning of this project.
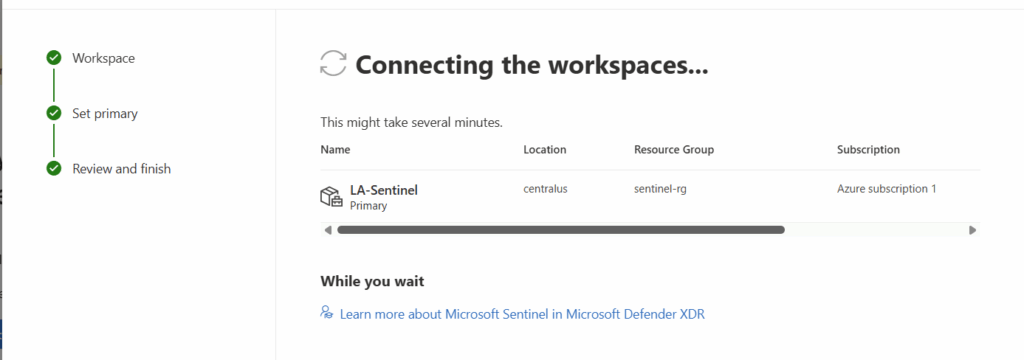
Microsoft Defender for Endpoint
Once onboarded to Defender XDR, we don’t have to make additional configurations for Defender for Endpoint. This is because the Unified Security Operations Platform leverages Defender XDR’s incident creation and correlation capabilities.
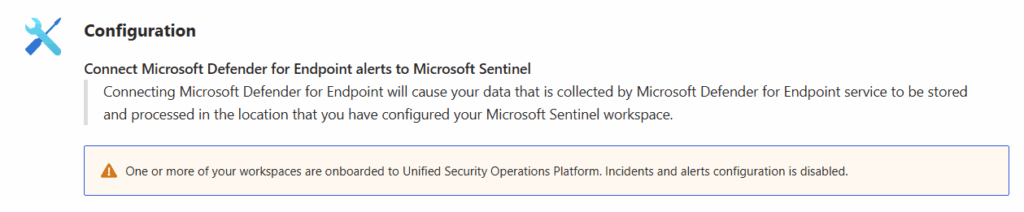
Microsoft Defender for Identity
Once onboarded to Defender XDR, we don’t have to make additional configurations for Defender for Identity. This is because the Unified Security Operations Platform leverages Defender XDR’s incident creation and correlation capabilities.
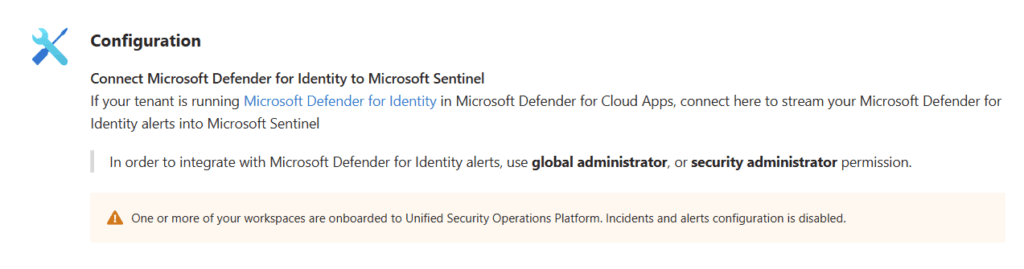
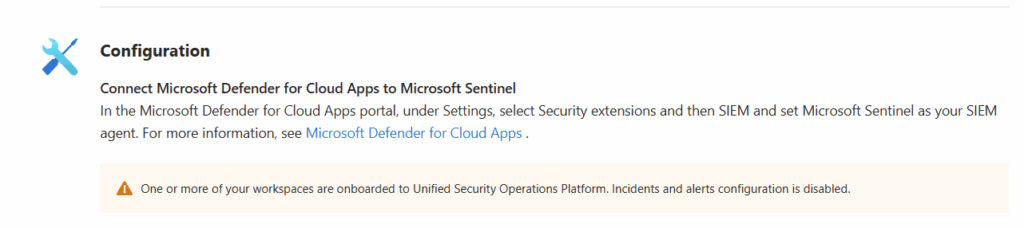
Microsoft Defender for Cloud Apps
Once onboarded to Defender XDR, we don’t have to make additional configurations for Defender for Cloud Apps. This is because the Unified Security Operations Platform leverages Defender XDR’s incident creation and correlation capabilities.
Conclusion
In conclusion, getting started with Microsoft Sentinel for free is an excellent opportunity for organizations to enhance their security posture without incurring initial costs. By leveraging the powerful capabilities of Microsoft Sentinel, you can gain comprehensive visibility into your security landscape, detect threats in real-time, and respond swiftly to incidents.
Don’t miss out on the chance to fortify your defenses and experience the benefits of a robust, cloud-native SIEM solution. Start your journey with Microsoft Sentinel today and take a proactive step towards securing your digital environment.


