Introduction
Identity security is and should be at the forefront of the strategy of IT managers, directors, and security staff. Threat actors are shifting their attack techniques to focus on the users’ identity to get into environments. To counteract this shift, Microsoft 365 and Entra ID have a license level called Entra ID Plan 1 (formerly known as Azure Active Directory Plan 1). This plan provides foundational IAM features to better protect your organization by enforcing security best practices while maintaining seamless user access to resources. Because of the robust offering of Entra ID plan 1, this is a critical component of a secure modern workplace.
In today’s post we will explore the features included in Entra ID plan 1 and we will detail the specific components that contribute to our secure modern workplace, M365 and beyond.
1. Multifactor Authentication (MFA)
One of the most critical components of any identity security strategy is Multi-Factor Authentication (MFA). Entra ID Plan 1 provides MFA capabilities that reduce the risk of compromised credentials by requiring users to verify their identity using a second factor, such as (in a preferred order too):
- A hardware security token (FIDO2 keys supported in higher plans)
- Biometric Security (Windows Hello for Business)
- Certificate Based Authentication
- A mobile app notification (Microsoft Authenticator)
- A text message (SMS) or phone call
Why is MFA Important?
MFA is important because stolen passwords are one of the many ways cybercriminals gain access. By implementing MFA, organizations can lower the risk of credential-based attacks like phishing and brute-force attacks. MFA does not solve for all attack types though. Security requires many layers because the latest attacks like session token stealing can circumvent MFA.
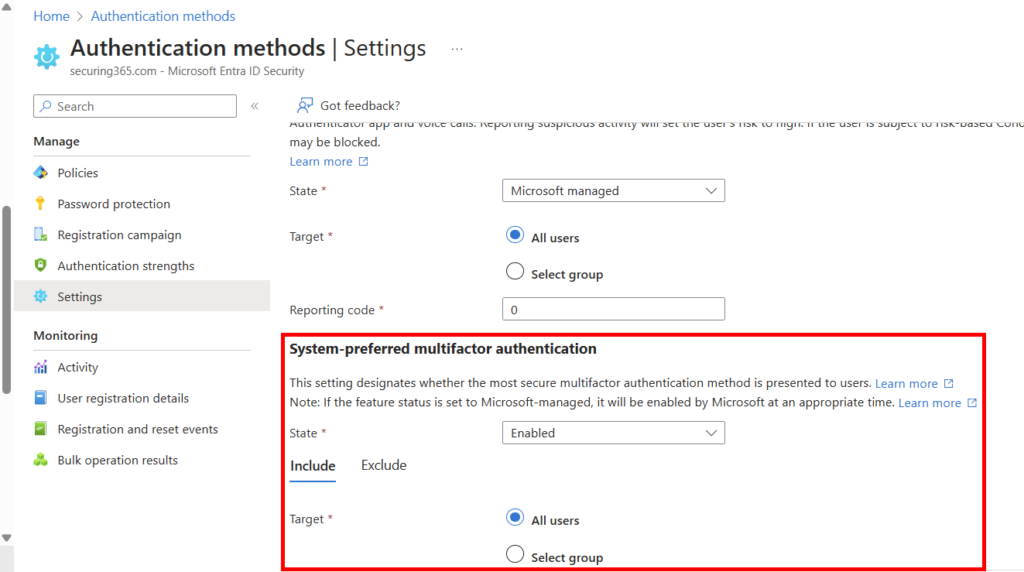
MFA Quick Tip:
Consider enabling the feature in Entra ID which prefers the more secure methods of MFA that a user has registered. The specific control is called: System-preferred multifactor authentication
2. Conditional Access Policies
Conditional Access (CA) is a powerful tool that enables organizations to enforce conditional security controls before granting access to resources. With Entra ID Plan 1, organizations can create policies that allow or block access based on factors such as:
- User identity and group membership (example: requiring MFA for high-privilege roles)
- Device compliance (example: requiring a compliant device for certain or all apps)
- Location (example: blocking sign-ins from locations outside of the U.S., Canada, or Mexico)
- Application sensitivity (example: requiring Windows Hello for Business for finance apps)
Why is Conditional Access Important?
Conditional Access provides granular control over who can access corporate resources and under what conditions, reducing the risk of compromised accounts leading to data breaches. It enables organizations to enforce a Zero Trust security model by verifying trust dynamically. Entra ID plan 1 is needed for conditional access, otherwise the granularity, specificity, and depth of security is limited in what organizations can deploy.
3. Single Sign-On (SSO)
Single Sign-On (SSO) is another key feature in Entra ID Plan 1 that enhances both security and user experience by enabling users to access multiple applications with a single set of credentials. Entra ID Plan 1 supports SSO across:
- Microsoft 365 applications
- Cloud-based SaaS applications (via SAML, OAuth, and OpenID Connect integration)
- On-premises applications (via Application Proxy)
Why is SSO important?
SSO reduces password fatigue, encourages strong authentication methods, and decreases the risk of credential reuse across multiple sites, thereby improving security and compliance. SSO is also a key step on the path to a passwordless environment. When users authenticate with Windows Hello for Business, they would then use SSO to get to all of their applications once authenticated.
4. Self-Service Password Reset (SSPR)
Self-Service Password Reset (SSPR) enables users to reset their passwords without needing IT support. This feature is a security and productivity enhancement, as it helps organizations:
- Reduce helpdesk workload related to password resets
- Ensure users can recover access to their accounts securely
- Enforce strong authentication for password recovery
SSPR can be configured to require users to verify their identity using multiple authentication methods, such as a mobile phone, email, or security questions. Organizations should consider adopting this as the ONLY way users can recover their password, otherwise their service desk employees may be prone to social engineering of the reset of passwords.
Why is SSPR important?
Password-related IT support tickets are among the most common in enterprise environments. SSPR not only saves IT time but also ensures a faster recovery process for users, reducing downtime maintaining a more secure process.
5. Device-Based Conditional Access (via Intune Integration)
Even though Microsoft Intune is a separate product, Entra ID Plan 1 allows organizations to enforce device-based Conditional Access Policies by integrating with Intune and enabling compliant device checks within policies. This enables security teams to enforce compliance policies that restrict access based on device health and management status.
Examples of policies include:
- Allowing access only from compliant devices
- Blocking access from jailbroken or rooted devices
- Enforcing device encryption and security baselines in Intune
Why is Device Compliance important?
Compromised and/or unmanaged devices are a major attack vector. By integrating Entra ID with Intune, organizations can ensure only trusted and secure devices access corporate resources. Think of it this way, 92% of Business Email compromises are from devices that are not organizationally owned. This is the single most fruitful way for an organization to protect their M365 access.
Conclusion
Microsoft Entra ID Plan 1 provides foundational security capabilities that help organizations secure identities, enforce Zero Trust principles, and enhance user experience. The key security features include:
- Multi-Factor Authentication (MFA)
- Conditional Access (CA)
- Single Sign-On (SSO)
- Self-Service Password Reset (SSPR)
- Device-Based Conditional Access (via Intune Integration)
For organizations looking to build a strong identity security foundation in Microsoft 365 and Azure environments, Entra ID Plan 1 is essential. While higher-tier plans (such as Entra ID Plan 2) offer advanced features like risk-based Conditional Access and Identity Protection, Plan 1 ensures that critical security controls that are less dynamic are in place to protect user accounts and corporate data.
Next Steps
If you’re not already using Entra ID Plan 1, consider evaluating its features to enhance your organization’s security posture. If you aren’t sure if you are licensed for Entra ID Plan 1, contact me using the link above.
For more insights on securing Microsoft 365, stay tuned to Securing 365 for the latest security updates and best practices!


